Article contents
The “Rock of Randomness”: a physical oracle for securing data off the digital grid
Published online by Cambridge University Press: 04 February 2019
Abstract
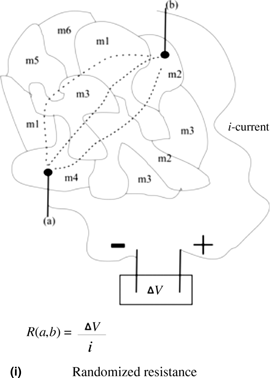
We propose a device to secure random data in analog format, so that it is taken off the digital grid. Such action will turn off the means by which remote hackers violate security. A physical “rock” manufactured through 3D printing technology, constructed on the basis of high-grade randomness, which is packed into the comprising materials of that rock. The rock functions as an oracle, and does not allow any massive copy of its content. Thus, a major claim of this Prospective is that materials science and engineering may hold the keys to the future of cryptography.
Information
- Type
- Prospective Articles
- Information
- Copyright
- Copyright © Materials Research Society 2019
Footnotes
G. Samid is also an adjunct professor in the Department of Electrical Engineering and Computer Science, Case Western Reserve University. Correspondence: gideon@bitmint.com or gideon.samid@case.edu
References
- 3
- Cited by

