1. Introduction
The type and function of rules that work to govern the commons effectively have been documented extensively in game-theoretic models, experiments, and case studies by Elinor Ostrom (Reference Ostrom1990, Reference Ostrom2005). Her work outlines eight design principles found across successful cases of self-governing communities, and categorizes the seven rule types used to implement these principles. The viability of the design principles often depends, however, on favorable conditions found in small, homogeneous communities whose right to self-govern is recognized by outside authorities (Araral, Reference Araral2014; McGinnis and Ostrom, Reference McGinnis, Ostrom, Biel, Eek, Garling and Gustafson2008).Footnote 1 Studies of communities where these conditions are not met can evidence the applicability and robustness of Ostrom's framework for self-governance under less favorable conditions (Leeson, Reference Leeson2008b; Skarbek, Reference Skarbek2016). Online communities provide one avenue for investigation (Kollock, Reference Kollock1998).
This paper provides a case study of online communities who share copyrighted material illegally – “pirates.” Pirate communities organize around BitTorrent, a peer-to-peer file-sharing protocol that relies on individual contribution to a shared resource in order to function. The communities are large, ranging from a few thousand to several million, with high rates of turnover, asymmetry of interests, and anonymous identities (Feldman et al., Reference Feldman, Lai, Stocia and Chuang2004). And, like their 18th-century namesake, these pirates are engaged in explicit illegal activity, preventing recourse through government institutions. Illegality and the threat of punishment, in fact, adds the largest cost and biggest obstacle to provision in the network.
Pirate networks thus represent a situation where the conditions for self-governance are less than ideal and government is an obstacle, not a benefit, for resource governance. As such, pirate networks represent a “hard case” for the discovery of mechanisms to prevent the tragedy of the commons (Boettke and Leeson, Reference Boettke and Leeson2004; Leeson and Subrick, Reference Leeson and Subrick2006). Despite these obstacles, pirate communities have established a series of rules that map well onto Ostrom's framework.
This paper is closely connected to the literature on internet governance (see Benson, Reference Benson2005; Christin, Reference Christin2012; Dourado and Tabarrok, Reference Dourado and Tabarrok2015; Hardy and Norgaard, Reference Hardy and Norgaard2016; Hess and Ostrom, Reference Hess and Ostrom2007; Kollock, Reference Kollock1998; Kollock and Smith, Reference Kollock, Smith and Herring1996; Mueller, Reference Mueller2010; Safner, Reference Safner2016). Kollock (Reference Kollock1998), for example, considers the difficulty of applying Ostrom's framework to online communities given the fluidity of identity and the difficulty in enforcing boundaries in online organizations. Kollock and Smith (Reference Kollock, Smith and Herring1996: 126) echo this sentiment in their study of how early Usenet newsgroups governed the “virtual commons,” concluding that “social organization [in] cyberspace has a double edge: monitoring . . . becomes easier while sanctioning . . . becomes more difficult; the costs of communication . . . are decreased while the effects of free-riding are often amplified.” More recently, however, both Dourado and Tabarrok (Reference Dourado and Tabarrok2015) and Safner (Reference Safner2016) use Ostrom's framework to explain the success of Wikipedia, suggesting that many of the difficulties of earlier online organizations can be overcome. My analysis contributes to this literature by demonstrating the robustness of Ostrom's framework for analyzing online governance in the “hard case” where illegality adds significantly to the cost of contribution and prevents an important design principle – the recognized right to govern – from being met.
2. Free-riding in peer-to-peer networks
Peer-to-peer (P2P) file sharing networks are used to distribute digital files between users without the need of a central server to act as a host. Files are transferred between users, known as peers, who act as both the server and client, supplying and consuming resources in the network. P2P networks avoid the large fixed costs associated with centralized hosting by distributing the disk storage, computing, and bandwidth costs among users (Pavlov and Saeed, Reference Pavlov and Saeed2004). When these networks are used to share copyrighted material illegally, the legal risk is also distributed; no single user is liable for hosting all the files and any node may be shut down without dismantling the whole network. A centralized network, in comparison, can be taken down by shutting down the single, central node, making centralized networks unattractive as a stable distribution mechanism for pirate activity.Footnote 2
P2P networks, while favored by pirates for the above features, also come with a cost: free-riding. P2P networks rely on the contribution of the individual peers to function. Contribution, including supplying bandwidth and adding new files to the network, is privately costly. In fact, users who contribute bandwidth to the network can see a significant increase in the time it takes to download a file. Feldman et al. (Reference Feldman, Lai, Chuang and Stoica2003), for example, estimate a fivefold increase in the time it takes to download a file if the user also uploads. Free-riding and the potential for the tragedy of the commons is thus a predictable result in P2P networks (Krishnan et al., Reference Krishnan, Smith and Telang2004; Nandi and Rochelandet, Reference Nandi and Rochelandet2009). In a study of an early P2P network, Gnutella, Adar and Huberman (Reference Adar and Huberman2000) found that nearly 70% of the users did not upload any files. They posited the possibility of a total network collapse if the trend continued. Hughes et al. (Reference Hughes, Coulson and Walkerdine2005) revisited the study years later and found that the number of free-riders on the network had increased to 85%.
A proposed solution to the free-riding problems in early P2P networks came from the development of a second-generation P2P architecture known as BitTorrent (Cohen, Reference Cohen2003; Kung and Wu, Reference Wu and Kung2003; Piatek et al., Reference Wu and Kung2007). Unlike previous protocols, BitTorrent forces a user to contribute. Once a piece of a file is transferred using BitTorrent, the user receiving the data must act as a host for download requests from other people – at least until the download is finished (Strahelivitz, Reference Strahilevitz2002). Peers who have finished downloading a file but continue to upload are called seeders. Peers who have not yet finished downloading a file are called leechers. As part of the BitTorrent protocol, users must seed (upload) while they leech (download). In addition to this change, BitTorrent has a built-in incentive mechanism designed after a tit-for-tat strategy (Cohen, Reference Cohen2003; Li et al., Reference Li, Yu and Wu2008). By the design of the protocol, peers are more likely to connect to and download from people they have previously uploaded to, potentially resulting in more connections and faster download speeds depending on the amount a peer contributes (Liu et al., Reference Liu, Dhungel, Wu, Zhang and Ross2010).
Compared to older P2P protocols, the built-in features of BitTorrent help encourage contribution, but free-riding issues remain (Anagnostakis et al., Reference Anagostakis, Harmantzis, Ioannidis and Zghaibeh2006; Andrade et al., Reference Andrade, Mowbray, Lima, Wagner and Ripeanu2005; Ripeanu et al., Reference Ripeanu, Mowbray, Andrade and Lima2006). For example, even with the forced-seeding feature, users may set their maximum upload speed to extremely low levels. Users thus upload, as required by the protocol, but contribute little to the actual bandwidth supply in the network. And while the tit-for-tat mechanism may discourage this behavior, it primarily does so only for the duration of the download and provides little incentive to seed after the download is complete. Once a user finishes downloading a file they can cease uploading all together (Kash et al., Reference Kash, Lai, Zhang and Zohar2012). As peers drop out from seeding, it is possible for a file to no longer be available on the network for any user, as a file needs at least one seed to remain accessible. Related is the issue of supplying the network with new files. Introducing new files to the network must rely on incentives external to the protocol as there are no built-in incentives to do so (Andrade et al., Reference Andrade, Santos-Neto, Brasileiro and Ripeanu2009; Meulpolder et al., Reference Meulpolder, D'Acunto, Capota, Wojciechowski, Pouwelse, Epema and Sips2010).
An additional problem not solved by the protocol relates to how bandwidth is allocated. Bandwidth supplied by individual peers in a P2P network is tied to the specific files they seed rather than across all files in the network, as it would be with centralized distribution. Total network supply – the available bandwidth across all files in the network – may exceed network demand, yet users may still experience congestion on files with a low number of seeds.Footnote 3 This congestion problem does not depend on the total number of users or total contribution level in the network and, unlike in a centralized network, cannot be solved by excluding non-payers. Even if access to the network is exclusive, the network resources remain rivalrous for those with access.Footnote 4
The free-riding problems not solved by the BitTorrent protocol may become less of an issue in the future as the cost of contributions in terms of disk storage, computing power, and bandwidth continue to fall. For pirates, however, these are not the only relevant costs. In a pirate network, the legal risk associated with sharing copyrighted material can add significantly to the cost of contribution (Bhattacharjee et al., Reference Bhattacharjee, Gopal, Lertwachara and Marsden2006; Feldman et al., Reference Feldman, Lai, Chuang and Stoica2003). P2P networks rely on individuals being able to identify and connect to other peers hosting the desired files, which means that companies attempting to enforce their copyright can join an existing torrent or upload their own copyrighted material as a way to identify and track pirates.Footnote 5 Once the IP address of a pirate is identified, the company can require the individual's ISP (internet service provider) to notify the user of copyright infringement. After multiple warnings, users caught pirating may have their internet speeds throttled, their internet service terminated, or they may even be sued. Pirates thus try to minimize the time spent actively seeding to reduce the probability of being caught. Pirates are also disincentivized from adding new files to the network as they can be severely punished for this.Footnote 6 Given the legal risk, it is no surprise that pirates contribute less than users in legal P2P networks (Ripeanu et al., Reference Ripeanu, Mowbray, Andrade and Lima2006).
To solve the problems not addressed by the protocol, pirates have organized into distinct communities that introduce a governance structure external to BitTorrent. Pirate communities center on tracker websites – The Pirate Bay being the most infamous example. A tracker is a server that communicates information to peers about peers by maintaining a list of who is seeding which files; it does not, however, host any of the illegal files. Most trackers are public, or open access, meaning anyone with an internet connection can download from the network. Other trackers are private, or allow selective access, meaning that membership is limited and access to the network is exclusive.
The ability to exclude is the main distinguishing factor between private and public trackers. In a public tracker, an individual's registered account may be suspended or banned, but that individual can still retain access to the network through non-registered use. Without the ability to exclude, public trackers lack a credible mechanism for rule enforcement and must instead rely on norms and the built-in mechanisms of BitTorrent to encourage contribution. Private trackers, on the other hand, have clearly defined boundaries with a credible enforcement mechanism of banishment. Private trackers can thus introduce and strictly enforce rules external to the protocol (Kash et al., Reference Kash, Lai, Zhang and Zohar2012; Rahman et al., Reference Rahman, Hales, Vinko, Pouwelse and Sips2010; Ripeanu et al., Reference Ripeanu, Mowbray, Andrade and Lima2006).
Several studies demonstrate that private trackers are more successful at mitigating free-riding than public trackers (see, Chen et al., Reference Chen, Jiang and Chu2010; Chen et al., Reference Chen, Chu and Li2011; Chen et al., Reference Chen, Chu and Liu2012; Meulpolder et al., Reference Meulpolder, D'Acunto, Capota, Wojciechowski, Pouwelse, Epema and Sips2010). Meulpolder et al. (Reference Meulpolder, D'Acunto, Capota, Wojciechowski, Pouwelse, Epema and Sips2010), for example, found download speeds to be three to five times faster in private trackers resulting from the significantly higher seeder-to-leecher ratios on the private sites. On average, the private trackers in their study had nearly 65 seeders per leecher compared to 4.6 in the public trackers. While numerous studies show the superiority of private trackers, few have discussed the internal governance structure that allows for their success.Footnote 7
3. Private trackers and their governance structure
Private trackers exist for almost every media format or subject matter and separate into distinct communities along these lines. Del.ish, for example, was a private tracker centered exclusively on food, with food-related television shows, movies, and books shared on the network. Public trackers instead tend to aggregate formats and subjects, acting as a “general” tracker for all media. The private communities investigated here are dedicated to the major media formats of music, movies, and television.
The private trackers investigated include PassThePopcorn (PTP), BroadcastheNet (BTN), and What.cd (WCD), which center on movies, television shows, and music respectively.Footnote 8 Each represent the “best” for their respective media, but are representative of private trackers in general.Footnote 9 When comparing the governance structure in private trackers and public trackers, The Pirate Bay (TPB), KickassTorrents (KAT) and h33t are used as examples.Footnote 10
All private trackers have explicitly written rules or “constitutions” (see Leeson and Skarbek, Reference Leeson and Skarbek2010; and Skarbek, Reference Skarbek2010, Reference Skarbek2011 on the use of constitutions in criminal organizations). Most sites have a list of “golden rules,” with additional pages dedicated to specific rules regarding less general matters. Within all three sites, the general rules include some statements declaring:
(1) members can only have one account per lifetime
(2) members must not share the torrent file on other networks
(3) members must not use a public proxy, Tor, or a free VPN to access the networkFootnote 11
(4) members must not sell invites
(5) members are expected to contribute.
In relation to (5), the general rules for PTP states, “Torrenting is a system of give and take, seeding and leeching – Please try to make sure you are uploading back the data you download . . . or uploading content of your own. Try to seed back at decent speeds.” BTN's rule (5) states, “We believe in sharing and encourage you to share as much as possible. If Staff feels that you aren't making a good faith effort to give back to the community your account may be penalized.” WCD has a broader rule (5) that declares, “Access to this website is a privilege, not a right, and it can be taken away from you for any reason.”
The general rules above are just the beginning of the pirate constitution. WCD, for example, has a 22,000+ word document outlining just the rules required for uploading new files. These general rules, and the specifics investigated below, set up a governance structure that clearly defines group boundaries, matches the rules governing resource use to the local conditions, provides effective incentives for group monitoring, and provides graduated sanctions for rule violation with a low-cost mechanism for conflict resolution. In other words, the governance structure in private pirate communities mimic many of Ostrom's (Reference Ostrom1990) design principles.
Below I use the rule types developed by Ostrom (Reference Ostrom2005) to categorize the rules found within private trackers, with an emphasis on the boundary, position, information, and payoff rules used by the sites.Footnote 12 The rules in WCD are similar to those in PTP and BTN, which are similar to those in other private trackers. As such, some rules will be discussed in generally when multiple sites share the same basic rule. Other rules are examined in more detail when there are major differences between rule forms.
For a pirate community to be considered successful in governing the commons, there are four main objectives that must be accomplished: (1) to encourage the contribution of bandwidth, particularly to low-seeded files (2) to encourage the introduction of new files to the network (3) to prevent malicious and mislabeled files, and (4) to prevent users from being tracked by copyright enforcers. The rules discussed below are structured in a way to achieve all four.
Boundary rules
Boundary rules define entrance eligibility and the process by which eligible members may enter or leave a community (Ostrom, Reference Ostrom2005: 194). Entrance to a private tracker is regulated through an invitation system designed to select for quality members. Seeding rates, even in the absence of explicit payoff rules, may be high if community selection is biased toward members likely to contribute (Asvanund et al., Reference Asvanund, Krishnan, Smith and Telang2004b).
New private communities may have an initial period of open access where any person may sign up; generally, only experienced pirates are aware of these opportunities. After a site obtains the desired number of members, the site will switch to invite only. Other new trackers may remain invite only from the start and recruit members exclusively from other private communities. Once a community is established, the ability to invite new members is reserved for advanced members of the site. In WCD, for example, a member will receive an invite to give out once they are promoted to Power User (see subsection “Position rules”). Additional invites may be obtained through further promotions or achievements.
Users are incentivized to be selective with their personal invites and risk losing their invite privileges or even their account if they invite poor-quality members. BTN, for example, has a rule that states, “You are responsible for the people you invite. If your invites are caught cheating . . . they will be banned and you will lose your invite privileges, at the very least.” After a series of rules specific to invites, BTN adds, “If you or your invitees are caught breaking one of these [invite] rules, you will be banned and your invite tree will be in danger.”
To aid in the selection of high-quality members in the environment of anonymous interaction and asymmetric information that is the internet, invite exchange and membership recruitment is often limited to specialized forums only accessible by high positioned members who have already demonstrated a willingness to contribute. Exchanging invites outside of the official invite forums is a bannable offense in all three of the private sites investigated.Footnote 13 For sites that do allow for trading invites outside of the official forums, potential candidates must signal their willingness to contribute through proof of a high upload-to-download ratio on another tracker and an internet speed test to demonstrate the candidate has the bandwidth availability to seed reliably. Both practices are often critiqued, as the selection mechanisms require a potential member to demonstrate their willingness to contribute before being given a chance to do so.
WCD has a unique boundary rule that partially corrects for this critique, causing WCD to be the first entry point into the private tracker world for many pirates. In addition to the traditional invite system, WCD offers the potential to gain access to the network by passing an interview. Interview questions range from technical questions on file types and compression techniques to WCD-specific rules and general Torrenting etiquette. The answers are more advanced than anything a contributing member would need to know, but the difficulty selects for high-quality members who may not have access to other effective signals. Individuals are allowed three chances to pass the interview and can take it every 48+ hours. The interview is timed, limiting the potential to look up answers. If someone fails on the third attempt, they may no longer attempt the interview process and can enter the site only by a personal invitation from an existing member.
The invitation system combined with the separation of communities by media format establishes distinct, yet connected, communities. Many users will join a tracker and work toward a promotion that grants entry to the invite forum as a way to gain access to a private tracker centered on a different media format. A cinephile, for example, may gain access to WCD through the interview process and contribute to the network for the primary purpose of gaining access to PTP. The nested structure and overlapping membership of these communities provides for a level of shared rules and culture, yet the local focus on distinct formats selects for users more dedicated to a particular media who are likely to have unique content to contribute – this is especially the case for niche trackers like Del.ish. In addition to sharing similar rules and members, many private trackers share the same web software, which causes them to look and function similarly and allows for ease of use across sites.Footnote 14
Boundary rules also aid in preventing unwanted members, specifically those who attempt to track users for copyright infringement. One way that private trackers deal with the issue of detection is by limiting the network size to limit their exposure. Most private trackers have a maximum number of users and will shut down the invite system once that number is reached. BTN, for example, lists a maximum of 35,000 users and has shut down the invitation system with 34,000+ members. PTP list a maximum of 30,000 users and WCD has a maximum of 200,000. The maximum is not a hard limit and can change depending on the network needs. PTP, for example, currently has more users than their listed maximum and WCD has increased their maximum several times throughout the years. Limiting the network size does, however, provide evidence for Asvanund et al.'s (Reference Asvanund, Clay, Krishnan and Smith2001, Reference Asvanund, Clay, Krishnan and Smith2004a) claim that P2P networks are bounded by the positive and negative externalities associated with membership size and Buchanan's (Reference Buchanan1965) claim on optimal exclusion more generally. Exposure is a negative externality of membership size that is often overlooked.
Additionally, the high cost of entry and the ability to ban users make private trackers less of a target for copyright enforcement, especially when public trackers, more populated in terms of numbers of users, are easy to enter owing to their open-access status. There is little reason, for example, to go through the process of interviewing at WCD to identify a few hundred individuals who may download a file when access to TPB is free and millions of people use the site. To the extent that copyright enforcers do gain access to private trackers, identification and banishment is possible. If multiple users receive a notification of copyright infringement, the administrators can cross-reference the users connected to that file to those connected to other files that were also monitored. If a user is consistently found across the monitored files, suggesting they may be the one tracking users, their account may be banned.
If a user is banned for any reason, they are not allowed back into the community as users are limited to one account per lifetime. The general rule banning public proxies and free VPNs limits the potential to circumvent this rule and provides for stronger boundary definition in the anonymous environment of the internet.
Boundary rules also specify how one may exit a community (Ostrom, Reference Ostrom2005: 198). For all trackers, members may voluntarily leave the community by not accessing the website and ceasing to seed any files. Most private trackers will disable accounts after a period of absence (typically 90 days). Disabled accounts may be reactivated by discussing the reasons for inactivity on the tracker's IRC (Internet Relay Chat) channel, a low-cost form of communication with administrators. IRC and forum messages function as the main forms of communication and dispute resolution between members and administrators.
Boundary rules in private trackers select for members likely to contribute to the network, limit exposure to copyright enforcement, and provide a level of shared enterprise between the distinct communities. By limiting users to one account and preventing the common methods of circumventing a ban, private trackers set up clearly defined boundaries with a credible mechanism for enforcing other rules.
Position rules
Position rules set out the type and number of positions available within a community, as well as the kind of authority each position may use (Ostrom, Reference Ostrom2005: 193). The concept of a tiered membership system is similar in both private and public sites. The degree of authority granted to each position, however, differs. Private trackers tend to have more positions and grant higher levels of authority, broader ranges of permissible activities, and larger increases in benefits with each promotion. Promotion is often used as a reward for continued contribution in the private network.
Public trackers do not require individuals to create an account to download from the network. Anyone that connects to the website can access the network's resources. Non-account-based users can search, download, and seed files. Registering an account grants new authority, such as the ability to upload new files and comment on forums or file listings.
Public trackers typically have some form of a “trusted” uploader position. These positions are granted based on the number of new files added to the network. h33t, for example, requires its members to upload ten unique files before they are promoted. The promotion comes with access to special forums and removes advertisements from the site. h33t claims there are “many more hidden benefits” with further promotions. Other public sites, such as TBP, provide no obvious benefits for being promoted and, instead of having set requirements, grant the trusted uploader position based on administer discretion. The position of trusted uploader in a public tracker aids in the search for quality content with less fear of mislabeled or malicious files and can be understood as an example in which position rules help correct for the inability to strictly enforce information rules.
Private trackers have multiple positions, each with accompanying privileges and requirements (see Figure 1). Promotion is determined by the amount of data seeded, the number of original files uploaded, and the amount of time a user has been a member. Higher-ranked positions require users to upload several unique files, demonstrating the user's ability to contribute desirable goods to the network. In PTP, a member can only be promoted to a Power User if they upload at least one unique file in addition to seeding 80 GiB of data.Footnote 15 Promotion to the next class, Elite User, requires 500 GiB seeded and 50 original uploads.

Figure 1. ‘User classes’ on PTP.
Promoted users gain access to restricted invite forums, additional site features (top 10s, custom titles and profile features, ability to create requests, etc.), and personal invites to give away to friends. Access to the invite forum, and thus additional private trackers, provides the largest benefit of promotion. In PTP, where the invite forums are restricted to positions that require original uploads, over 35% of the total users on the network have uploaded at least one original file (see Figure 2).Footnote 16 Towards the very upper tier of positions, little is left to give in terms of granting new permissions or benefits. Achieving the highest rank in a private tracker is more a contest in reputation than explicit payoff gains. BTN, for example, has the position of Overlord for which a user must have a total data transfer of over 100 TB with a least 250,000 days of total seed time (across all files) and have downloaded more than 35,000 files. The class below Overload, Master, only requires 7.5 TB and 3,000 files downloaded. Both positions come with similar privileges.
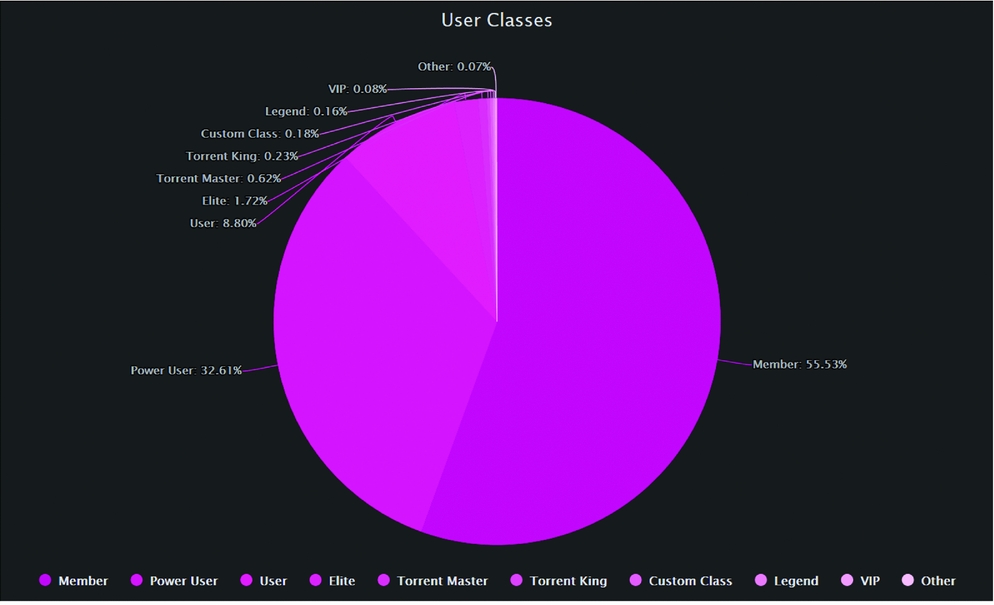
Figure 2. Percentages of ‘user classes’ on PTP.
Position rules also determine how many individuals may participate in each position (Ostrom, Reference Ostrom2005: 193). Most private trackers do not have a specified limit for each position and instead allow for the number to remain fluid. In a closed-invite system with a maximum number of users, there is a trend of decreasing lower classes and increasing higher classes over time (see Figure 3). In BTN, for example, the number of users in the upper half of the position tier (Overlord, Master, Guru, Elite) is similar to the number in the lower half (Extreme User, Power User, Member, User). Additionally, the number of Power Users, Extremes, Elites, Gurus, and Masters each individually outweighs the number of Users or Members. Only the highest position, Overlord, has fewer users than the lowest position.
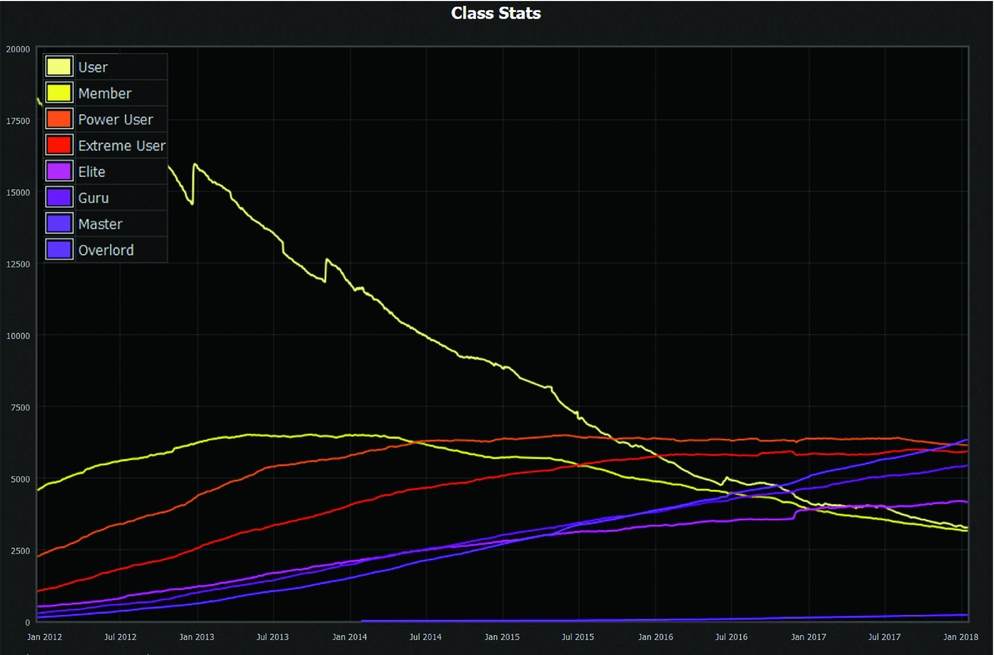
Figure 3. ‘Class stats’ on BTN.
Positions within pirate communities are determined by willingness to contribute to the network. Increases in permissible activities and privileges associated with promotion encourages contribution. Restricting valuable privileges, such as the invite forums, to positions that require original uploads incentivizes adding new content to the network.
Information rules
Information rules delegate the authorized channels for the flow of information and influence the accuracy of information by obligating minimal requirements of communication (Ostrom, Reference Ostrom2005: 206). Information rules in pirate communities are used primarily to regulate quality assurance and communicate the potential for malicious files or files to be tracked by copyright enforcers.
Most trackers have rules in place specifying the way a file should be labeled. KAT, for example, requires uploaders to specify the file size, format, quality, and source of origin (e.g. 5.3GiB, .MKV, 720p, Blu-ray). They are also expected to provide an accurate title that reflects this information. The formal information rules in public trackers are, however, not well enforced and the information provided is often incorrect. Nevertheless, users within public trackers have developed norms to correct for inaccuracies using other information avenues.
The comment section on a file listing provides one such avenue. The comment section for a wrongfully labeled file in a public tracker tends to be filled with angry postings about inaccurate information and wasted time or bandwidth. Users will often comment on the quality of the file (a ranking out of ten for the audio or video quality) to warn other users if it is not worth downloading. Additionally, users will comment if the file registered on their anti-virus program, alerting other users of potentially malicious files. Checking the comment section before downloading any file on a public tracker becomes common practice and a shared strategy among users. Constant violators of quality norms are often quickly warned against. Conversely, on private sites, where the formal informational rules are better enforced, the comment section is used less for valuable information exchange and more for discussing the media content. Rather than comments about inaccurate labeling, file quality, or malicious files, the comment section in a private tracker is filled with personal opinions on whether, for example, a movie is worth watching.
Some public trackers, such as KAT, provide formal reputation mechanisms to correct for information inaccuracies. KAT explains its reputation system as the “overall measure or site-rank that gives an indication of your activity on the KickassTorrents web-site.” Users gain reputation points for “rating as well as leaving torrent comments, reporting such things as Faker Users, Infected Torrents, Spam Comments etc.” The reputation rating is displayed next to a user's name, allowing users to see the reputation of the uploader before downloading a file. KAT also has an up- and downvoting system in place for every file listing, so users can rate the file as good (upvote) or bad (downvote). These mechanisms work to aggregate what can be found informally in the comment section of other public sites. In reference to the importance of its reputation system, KAT's FAQ states: “If you are a committed Kickass Member you know the value of being able to look at the feedback given to a torrent and making your choice whether to download or not based not only on who uploaded it, but their reputation and that of the members who gave feedback.”Footnote 17 h33t takes another, costlier, approach to quality assurance that is rarely found in public trackers but is common in private ones: h33t has a moderator check every file before it is allowed to be listed on the tracker.
Beyond quality assurance, whether a file is being monitored by companies looking to enforce their copyright is an important information signal necessary for individuals in a pirate community to avoid punishment. Individuals who receive a notification of copyright infringement from a file on a public track will often use the informal comment section to warn others. There is, however, no explicit payoff incentive to share this information. Altruism and perhaps the pleasure gained from helping individuals further the sharing culture undetected may encourage this behavior (see Ripeanu et al., Reference Ripeanu, Mowbray, Andrade and Lima2006 for a discussion on altruism and gifting motivations in the context of pirate networks).
Compared to public trackers, private trackers have more specific information rules. WCD, for example, has a 22,000+ word document outlining the rules required for uploading a new file. Some of the specifications include which bitrates and audio containers are allowed; how to label non-standard files, such as a live or bootleg album; and how to organize and label the songs within an album folder. Private trackers also have some form of acceptable minimum quality for files with specific types of media and sources prohibited. WCD does not allow music files below a 128 bitrate. Pre-retail movies, such as cam recordings – live recordings of a movie as it airs in the theater – are banned on PTP. These enforced information rules help assure at least a minimum level of quality on the private sites.
While users may be banned in private trackers for continual violation of information rules, the payoff rules discussed in the next section provide incentives for group monitoring and enforcement. Private trackers allow for the “trumping” of a mislabeled or poor-quality file. A file may be trumped for numerous reasons. PTP lists over twenty reasons including hard-coded subtitles, improper aspect ratios, and better-quality files being released (e.g. a Blu-ray file trumps a HDTV file). Users, in the quest for more upload credit, actively search out mislabeled and poor-quality files to trump. Information rules in private trackers are thus monitored and enforced by the members with minimal effort from moderators.
Payoff rules
Payoff rules assign rewards or sanctions to actions (Ostrom, Reference Ostrom2005: 207). Public trackers cannot effectively apply sanctions and have very low reward structures for contributions to the network. Position ranks may be the only actual differentiation between a contributing member and a free-rider in a public tracker. The privileges assigned to these positions are, however, not very useful and, for most users, unlikely to be enough of a payment for the risk borne by continuously sharing and introducing new files to a public network.
Private trackers change this dynamic by providing a reward system and requiring a minimum level of contribution to retain access to the network. Most private sites have a Sharing Ratio Enforcement (SRE) mechanism which requires members to upload a given amount of data for every bit of data they download (Chen et al., Reference Chen, Chu and Liu2012; Meulpolder et al., Reference Meulpolder, D'Acunto, Capota, Wojciechowski, Pouwelse, Epema and Sips2010).Footnote 18 Each member is assigned a unique passkey that allows the tracker to monitor a user's upload and download activity. Sharing the passkey is a bannable offense. If multiple IP addresses are identified on the same passkey, the account may be investigated for suspicious activity. The upload and download information is automatically updated and graduated sanctions are applied to users who fall below the required ratio. Users who fall below the required ratio are first warned. After multiple warnings, the user is put on ratio watch. A user who is on ratio watch will lose access to the privileges associated with their current position and will eventually be banned if their ratio does not improve.
Ratio requirements do not apply to new members until they have downloaded a certain amount of data. This amount differs between sites depending on the average file size and formats used. The ratio requirement in WCD, for example, does not apply until a user has downloaded +5 GB of data. When the average file size is much larger, such as with high-definition movies or television shows, the ratio requirement may not apply until more downloading has occurred (say 10–30 GB). Once the SRE does apply, the required ratio changes depending on how much a user downloads. Higher levels of total download require higher ratios (see Figure 4).

Figure 4. ‘Required ratio table’ on What.cd.
Some private trackers also apply a lower ratio requirement for users who seed 100% of the files they download. Consider two members of WCD: one who seeds every file they download and the other who does not. If both users download 50 GB of data, the user who seeds every file would need to upload 10 GB to maintain the required ratio of 0.2. The user who does not seed every file must maintain a higher ratio of 0.5 and would be required to upload at least 25 GB of data to retain access to the network. This mechanism assures that files will remain accessible on the network as users, especially those without the bandwidth availability to upload at high speeds, are incentivized to seed even if the files are currently not in high demand.
Not every successful private tracker requires a ratio. Due to the large file size of television shows, the frequency at which shows air, and the lack of interest in older episodes after a few days or weeks, BTN users are not required to maintain an upload-to-download ratio. Instead, users are required to seed for a set period of time. For a single TV episode, users are required to seed the file for at least 24 hours or until they reach to a 1:1 ratio. For full TV seasons, users must seed for 120 hours or to a 1:1 ratio. The seed time does not have to be continuous, but a “hit and run” (seeding less than the required time and/or ratio) will be recorded if the member does not meet the seeding requirement within two weeks of downloading the file. After a user obtains 15 hit and runs, their account will be banned. This time-seeded method was one of the alternative methods suggested by Golle et al. (Reference Golle, Leyton-Brown, Mironov and Lillibridge2001) as a potential mechanism to mitigate free-riding in P2P networks. It also appears to be successful: BTN generally maintains a seeder-to-leecher ratio above 150, similar to both PTP and WCD.
Nevertheless, time requirements may not be as effective as SREs (Jia et al., Reference Jia, Rahman, Vinko, Pouwelse and Epema2011). Like with BitTorrent's forced-seeding feature, users may seed for the tracker's required time but set their upload speed to low levels (Ripeanu et al., Reference Ripeanu, Mowbray, Andrade and Lima2006). To correct for this, BTN and other sites incentivize seeding beyond the required time or ratio requirement by offering bonus points. Bonus points can be used to purchase things like hit-and-run removals, additional invites, or site features (see Figure 5). Upload credit (upload beyond a required ratio) for trackers with SREs and bonus points for those without become the currency within these sites, and are used as rewards for contribution to the network.
Figure 5. ‘Bonus points’ shop on PTP.
The reward system is also used to incentivize the introduction of new files to the network. Private trackers have a request system that allows individual members to request files not currently on the network and set a bounty in whatever currency the site uses. Other members can contribute to the bounty if they also desire the file. The top request on PTP offers over 80 TiB of upload credit to the person who uploads Cristal de souffrance, a 1978 short film by Michel Houellebecq. This bounty is the equivalent of being able to download over 16,000 720p Blu-ray movies – around 5GiB per movie – before the user's ratio is negatively affected. Members can fill this request by whatever means possible, so long as the file they upload meets all the minimal requirements for both the site and the request. Individuals attempting to fulfill the request may engage in arbitrage by taking from other markets – other private trackers, public trackers, or the legal private goods market – where the price of obtaining the file is valued less than the bounty. Filling a request counts as an original upload and is often a quick way for users to gain the uploads required for promotion. Gaining a promotion through fulfilling a request adds to the value of introducing new files to the network beyond the listed bounty.
The structure of the rewards system also encourages contribution to files with a low number of seeds. Consider, for example, two files of the same size, one with only one seed, file A, and the other with ten seeds, file B. If a user downloads file A, the single seeder is guaranteed the full file size in upload credit. If a user downloads file B and connects to more than one seed, each seeder will be credited less than the full size. Assuming a user connects to every seed and downloads equally from each, ten users would have to download file B before the seeders receive the same amount of upload credit as the single seeder on file A. While many users seed popular files to gain more upload credit, seeding a less popular file with a low number of seeds can pay off similarly. BTN, being a ratioless tracker, incentivizes seeding low-seeded files in a different way: BTN adds a multiplier to the bonus point formula for seeding a file with less than five seeds.
The incentive to seed files combined with the request system make private trackers superior for harder-to-find files. For example, of Empire's list of 25 movies that never made it from VHS to DVD, PTP has all but one movie actively seeded.Footnote 19 The Pirate Bay, the largest public tracker, is missing ten. Further, of the 15 movies on both trackers, TPB only beat PTP in the number of seeds on one movie – and here it should be noted that TPB has an estimated 50 million users compared to PTP's 34,000.Footnote 20 Additionally, because users are incentivized to obtain upload credit, seeders in a private tracker often allot more bandwidth to uploading compared to seeders in a public tracker, meaning that not only can users find rare files in private trackers, they also experience faster speeds.
All private sites investigated have some form of required seeding with accompanying rewards and sanctions. The differences in these rules provide an example of matching the rules governing resource use to the local conditions. The use of ratios, whether upload- or time-based, encourages users to contribute bandwidth to the network. Additional features like requiring lower ratios for users who continue to seed every file and building in a multiplier to the bonus point formula incentivize users to seed files with a low number of seeds. The request system encourages the introduction of new files to the network.
4. How do public trackers survive?
If the use of boundary, position, information, and payoff rules are what allow private sites to function smoothly and public sites either lack these rules altogether or have weak, poorly enforced versions, how do public sites survive?
What private sites achieve with enforceable rules, public sites make up for with a reliance on the built-in features of the BitTorrent protcol, reliance on the norms discussed in section 3, and their sheer size. The Pirate Bay, for example, had an estimated 50 million users in 2014. If even a small fraction of these users remain seeding – whether from ignorance of how BitTorrent works, forgetting to delete the torrent file, a commitment to the sharing culture, or living in a region with less enforcement – the network can maintain itself, albeit with significantly slower download speeds given the higher number of free-riders, more malicious files given the inability to ban malicious users, less unique content given the lack of an incentive to contribute new files, and a higher chance of users being caught or trackers being taken down given the increased exposure that comes with a large user base and open access network.
Nevertheless, there are steps that users take to limit their risk of contributing to a network. A VPN, for example, is a suggested purchase for frequent users of public trackers. Additional programs, like Peerblock, which block incoming and outgoing connections to IP addresses on a blacklist, are also a common strategy, which are, however, fairly easy to circumvent and come with the cost of blocking large groups of potentially safe connections. Another strategy taken by the more risk-averse users in a public tracker is being selective with what they download and avoiding recent, popular files from companies with a known strategy of enforcement. Downloading the most recent episode of Game of Thrones is more likely to get a user caught than downloading a television show from the 1990s. This strategy, while potentially effective, has its downsides if the user wants to consume the newest content.
For trackers, a general strategy is to host the server in a region where the legality of such a site is more ambiguious and enforcement more lax. Most trackers do not host the server in the United States nor do they have a .com domain extension. Instead, they register the domain and host the servers from countries like Montenegro (.me), the Phillipines (.ph), Sweden (.to) or the Democratic Republic of the Congo (.cd).Footnote 21 Further, because trackers do not host the files themselves and the actual amount of data required for keeping the ledger is small, sites that are taken down or shut down for other reasons can be easily reopened shortly after.
Most trackers also have some declaration disavowing themselves of copyright infringement. PTP, for example, states, “None of the files shown here are actually hosted on this server. The links are provided solely by the sites’ users. . . . The administrator of this site . . . holds NO RESPONSIBILITY if these files are misused in any way and cannot be help responsible for what its users post.” TPB claims, “No torrent files are saved at the server. That means no copyrighted and/or illegal material are stored by us. It is therefore not possible to hold the people behind The Pirate Bay responsible for the material that is being spread using the site.” These disclaimers, however, have had little success in preventing other trackers from being shut down.
5. Conclusion
That communities can self-organize to solve collective action problems and secure cooperation is not controversial if we assume favorable conditions. However, as conditions drift further from ideal, such as when P2P networks are used to illegally share copyrighted material, the standard predicted level of cooperation tends toward zero. Early models and predictions of P2P networks suggested complete collapse as the dominant strategy was always to defect.
Pirate communities have been able to overcome these challenges by clearly defining group boundaries, matching the rules governing resource use to the local conditions, and providing effective incentives for group monitoring with graduated sanctions for rule violation. Through the use of boundary, position, information, and payoff rules, these communities have been able to govern the commons with relative success and stability. BTN, for example, has continued to operate since 2009, and while The Pirate Bay has been shut down many times, the founders even arrested, the community has continued for close to 14 years with a high profile and under constant legal threat.
Understanding how pirate communities self-organize and develop institutional mechanisms to ensure cooperation under conditions that are far from ideal can help understand governance and cooperation under all types of constraints. While many of the early problems associated with online governance can be solved through technological advancements that reduce anonymity and allow for stricter boundary enforcement, other problems require institutional solutions. Ostrom's framework, even in the “hard case,” is applicable to understanding how online communities solve issues of free-riding and effectively govern the commons.
Acknowledgments
I would like to thank Adam Martin, Peter Leeson, Christopher Coyne, Geoffrey Hodgson, and three anonymous referees for their helpful comments and suggestions.






