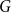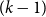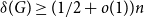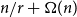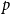Refine search
Actions for selected content:
6950 results in Algorithmics, Complexity, Computer Algebra, Computational Geometry
10 - Further Research
-
- Book:
- Proof Complexity Generators
- Published online:
- 29 May 2025
- Print publication:
- 26 June 2025, pp 104-110
-
- Chapter
- Export citation
7 - The Case of ER
-
- Book:
- Proof Complexity Generators
- Published online:
- 29 May 2025
- Print publication:
- 26 June 2025, pp 58-74
-
- Chapter
- Export citation
9 - Contexts
-
- Book:
- Proof Complexity Generators
- Published online:
- 29 May 2025
- Print publication:
- 26 June 2025, pp 93-103
-
- Chapter
- Export citation
On the size of temporal cliques in subcritical random temporal graphs
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 34 / Issue 5 / September 2025
- Published online by Cambridge University Press:
- 26 June 2025, pp. 671-679
-
- Article
- Export citation
4 - The Stretch
-
- Book:
- Proof Complexity Generators
- Published online:
- 29 May 2025
- Print publication:
- 26 June 2025, pp 30-41
-
- Chapter
- Export citation
Dedication
-
- Book:
- Proof Complexity Generators
- Published online:
- 29 May 2025
- Print publication:
- 26 June 2025, pp v-vi
-
- Chapter
- Export citation
Special Symbols
-
- Book:
- Proof Complexity Generators
- Published online:
- 29 May 2025
- Print publication:
- 26 June 2025, pp 111-113
-
- Chapter
- Export citation
Contents
-
- Book:
- Proof Complexity Generators
- Published online:
- 29 May 2025
- Print publication:
- 26 June 2025, pp vii-x
-
- Chapter
- Export citation

Oriented Matroids
-
- Published online:
- 04 June 2025
- Print publication:
- 10 April 2025

Games of No Chance 4
-
- Published online:
- 30 May 2025
- Print publication:
- 16 April 2015

Algorithmic Number Theory
- Lattices, Number Fields, Curves and Cryptography
-
- Published online:
- 30 May 2025
- Print publication:
- 20 October 2008
Tight Hamilton cycles with high discrepancy
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 34 / Issue 4 / July 2025
- Published online by Cambridge University Press:
- 30 May 2025, pp. 565-584
-
- Article
-
- You have access
- Open access
- HTML
- Export citation

More Games of No Chance
-
- Published online:
- 29 May 2025
- Print publication:
- 25 November 2002

Proof Complexity Generators
-
- Published online:
- 29 May 2025
- Print publication:
- 26 June 2025
Short proof of the hypergraph container theorem
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 34 / Issue 5 / September 2025
- Published online by Cambridge University Press:
- 16 May 2025, pp. 621-624
-
- Article
- Export citation

Quantum Algorithms
- A Survey of Applications and End-to-end Complexities
-
- Published online:
- 03 May 2025
- Print publication:
- 24 April 2025
-
- Book
-
- You have access
- Open access
- Export citation

An Introduction to String Diagrams for Computer Scientists
-
- Published online:
- 01 May 2025
- Print publication:
- 29 May 2025
-
- Element
-
- You have access
- Open access
- HTML
- Export citation

Data Structures and Algorithms Using Python
-
- Published online:
- 30 April 2025
- Print publication:
- 15 June 2023
-
- Textbook
- Export citation
Colouring random subgraphs
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 34 / Issue 4 / July 2025
- Published online by Cambridge University Press:
- 28 April 2025, pp. 585-595
-
- Article
- Export citation
17 - Loading classical data
- from Part II - Quantum algorithmic primitives
-
- Book:
- Quantum Algorithms
- Published online:
- 03 May 2025
- Print publication:
- 24 April 2025, pp 255-269
-
- Chapter
-
- You have access
- Open access
- Export citation