Refine search
Actions for selected content:
48533 results in Computer Science
2 - Wireless security
-
- Book:
- Security and Quality of Service in Ad Hoc Wireless Networks
- Published online:
- 26 February 2010
- Print publication:
- 06 March 2008, pp 17-42
-
- Chapter
- Export citation
6 - Quality of service
-
- Book:
- Security and Quality of Service in Ad Hoc Wireless Networks
- Published online:
- 26 February 2010
- Print publication:
- 06 March 2008, pp 107-128
-
- Chapter
- Export citation
4 - Trust management
-
- Book:
- Security and Quality of Service in Ad Hoc Wireless Networks
- Published online:
- 26 February 2010
- Print publication:
- 06 March 2008, pp 61-81
-
- Chapter
- Export citation
Contents
-
- Book:
- Security and Quality of Service in Ad Hoc Wireless Networks
- Published online:
- 26 February 2010
- Print publication:
- 06 March 2008, pp vii-x
-
- Chapter
- Export citation
5 - Intrusion detection
-
- Book:
- Security and Quality of Service in Ad Hoc Wireless Networks
- Published online:
- 26 February 2010
- Print publication:
- 06 March 2008, pp 82-106
-
- Chapter
- Export citation
Frontmatter
-
- Book:
- Security and Quality of Service in Ad Hoc Wireless Networks
- Published online:
- 26 February 2010
- Print publication:
- 06 March 2008, pp i-vi
-
- Chapter
- Export citation
8 - Security in WiMax networks
-
- Book:
- Security and Quality of Service in Ad Hoc Wireless Networks
- Published online:
- 26 February 2010
- Print publication:
- 06 March 2008, pp 147-171
-
- Chapter
- Export citation
A Note on Freĭman's Theorem in Vector Spaces
-
- Journal:
- Combinatorics, Probability and Computing / Volume 17 / Issue 2 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 297-305
-
- Article
- Export citation
HM(X) type inference is CLP(X) solving
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 18 / Issue 2 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 251-283
-
- Article
-
- You have access
- Export citation
Constraint Logic Programming using ECLiPSeKrzysztof Apt and Mark Wallace Cambridge University Press, 2007 Hardback: ISBN 9780521866286, Price: £35, 348 pages.
-
- Journal:
- Theory and Practice of Logic Programming / Volume 8 / Issue 2 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 242-246
-
- Article
- Export citation
A type system with usage aspects
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 18 / Issue 2 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 141-178
-
- Article
-
- You have access
- Export citation
An Analysis of the Height of Tries with Random Weights on the Edges
-
- Journal:
- Combinatorics, Probability and Computing / Volume 17 / Issue 2 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 161-202
-
- Article
- Export citation
On the Number of Tetrahedra with Minimum, Unit, and Distinct Volumes in Three-Space
-
- Journal:
- Combinatorics, Probability and Computing / Volume 17 / Issue 2 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 203-224
-
- Article
- Export citation
Improving Prolog programs: Refactoring for Prolog
-
- Journal:
- Theory and Practice of Logic Programming / Volume 8 / Issue 2 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 201-215
-
- Article
- Export citation
The Random-Cluster Model, by Geoffrey Grimmett, Springer, 2006, 377pp., £69.00/$125.00/89.95 Euros.
-
- Journal:
- Combinatorics, Probability and Computing / Volume 17 / Issue 2 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 317-318
-
- Article
- Export citation
Situational reasoning for task-oriented mobile service recommendation
-
- Journal:
- The Knowledge Engineering Review / Volume 23 / Issue 1 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 7-19
-
- Article
- Export citation
Semantically routing queries in peer-based systems: the H-Link approach
-
- Journal:
- The Knowledge Engineering Review / Volume 23 / Issue 1 / March 2008
- Published online by Cambridge University Press:
- 01 March 2008, pp. 51-72
-
- Article
- Export citation
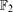 . Specifically we show that if
. Specifically we show that if 
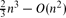 , and there are point sets for which this number is
, and there are point sets for which this number is 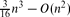 . We also present an
. We also present an 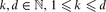 , the maximum number of
, the maximum number of 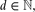 , the minimum number of distinct volumes of all full-dimensional simplices determined by
, the minimum number of distinct volumes of all full-dimensional simplices determined by 