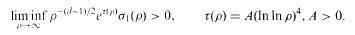Refine search
Actions for selected content:
9084 results in Discrete Mathematics, Information Theory and Coding
Rational points on the superelliptic Erdös Selfridge curve of fifth degree
- Part of
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 113-124
- Print publication:
- December 2003
-
- Article
- Export citation
MTK volume 50 issue 1-2 Cover and Front matter
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. f1-f4
- Print publication:
- December 2003
-
- Article
-
- You have access
- Export citation
Characterization of ellipsoids and polarity in convex sets
- Part of
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 63-72
- Print publication:
- December 2003
-
- Article
- Export citation
Counting points of bounded relative height
- Part of
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 125-152
- Print publication:
- December 2003
-
- Article
- Export citation
Unbounded analytic functions on plane domains
- Part of
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 207-214
- Print publication:
- December 2003
-
- Article
- Export citation
On the geometric structure of convex sets with the RNP
- Part of
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 73-85
- Print publication:
- December 2003
-
- Article
- Export citation
Intrinsic harmonicily of Morse functions
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 167-170
- Print publication:
- December 2003
-
- Article
- Export citation
On a lattice point problem arising in the spectral analysis of periodic operators
- Part of
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 87-98
- Print publication:
- December 2003
-
- Article
- Export citation
The form of the spectral functions associated with Dirac equations
- Part of
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 153-165
- Print publication:
- December 2003
-
- Article
- Export citation
How can we recover Baire class one functions?
- Part of
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 171-198
- Print publication:
- December 2003
-
- Article
- Export citation
When do sections of different dimensions determine a convex body?
- Part of
-
- Journal:
- Mathematika / Volume 50 / Issue 1-2 / December 2003
- Published online by Cambridge University Press:
- 26 February 2010, pp. 35-55
- Print publication:
- December 2003
-
- Article
- Export citation
24 - Applying the MPT in Bifurcation Problems
-
- Book:
- The Mountain Pass Theorem
- Published online:
- 04 September 2009
- Print publication:
- 15 September 2003, pp 288-295
-
- Chapter
- Export citation
Index
-
- Book:
- The Mountain Pass Theorem
- Published online:
- 04 September 2009
- Print publication:
- 15 September 2003, pp 365-369
-
- Chapter
- Export citation
2 - Palais-Smale Condition: Definitions and Examples
-
- Book:
- The Mountain Pass Theorem
- Published online:
- 04 September 2009
- Print publication:
- 15 September 2003, pp 15-21
-
- Chapter
- Export citation
14 - The Semismooth MPT
-
- Book:
- The Mountain Pass Theorem
- Published online:
- 04 September 2009
- Print publication:
- 15 September 2003, pp 163-173
-
- Chapter
- Export citation
11 - Symmetry and the MPT
-
- Book:
- The Mountain Pass Theorem
- Published online:
- 04 September 2009
- Print publication:
- 15 September 2003, pp 114-133
-
- Chapter
- Export citation
Bibliography
-
- Book:
- The Mountain Pass Theorem
- Published online:
- 04 September 2009
- Print publication:
- 15 September 2003, pp 323-364
-
- Chapter
- Export citation
II - Reaching the Mountain Pass Through Easy Climbs
-
- Book:
- The Mountain Pass Theorem
- Published online:
- 04 September 2009
- Print publication:
- 15 September 2003, pp 45-46
-
- Chapter
- Export citation
Frontmatter
-
- Book:
- The Mountain Pass Theorem
- Published online:
- 04 September 2009
- Print publication:
- 15 September 2003, pp i-viii
-
- Chapter
- Export citation
III - A Deeper Insight in Mountains Topology
-
- Book:
- The Mountain Pass Theorem
- Published online:
- 04 September 2009
- Print publication:
- 15 September 2003, pp 91-92
-
- Chapter
- Export citation
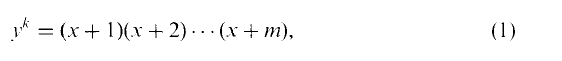
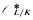 be the subgroup of the unit group
be the subgroup of the unit group 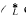 consisting of the elements that are roots of units of
consisting of the elements that are roots of units of 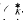 . Denote by
. Denote by 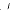 (
(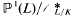 with relative height in the sense of Bergé-Martinet at most
with relative height in the sense of Bergé-Martinet at most 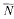 (ρ) the number
(ρ) the number 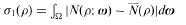 for dimensions
for dimensions