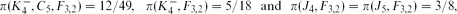Refine search
Actions for selected content:
48287 results in Computer Science
2 - Inductive Definitions
- from Part I - Judgments and Rules
-
- Book:
- Practical Foundations for Programming Languages
- Published online:
- 05 February 2013
- Print publication:
- 17 December 2012, pp 11-19
-
- Chapter
- Export citation
16 - Recursive Types
- from Part V - Infinite Data Types
-
- Book:
- Practical Foundations for Programming Languages
- Published online:
- 05 February 2013
- Print publication:
- 17 December 2012, pp 116-124
-
- Chapter
- Export citation
42 - Concurrent Algol
- from Part XVI - Concurrency
-
- Book:
- Practical Foundations for Programming Languages
- Published online:
- 05 February 2013
- Print publication:
- 17 December 2012, pp 363-372
-
- Chapter
- Export citation
3 - Hypothetical and General Judgments
- from Part I - Judgments and Rules
-
- Book:
- Practical Foundations for Programming Languages
- Published online:
- 05 February 2013
- Print publication:
- 17 December 2012, pp 20-28
-
- Chapter
- Export citation
MSC volume 23 issue 1 Cover and Front matter
-
- Journal:
- Mathematical Structures in Computer Science / Volume 23 / Issue 1 / February 2013
- Published online by Cambridge University Press:
- 14 December 2012, pp. f1-f2
-
- Article
-
- You have access
- Export citation
MSC volume 23 issue 1 Cover and Back matter
-
- Journal:
- Mathematical Structures in Computer Science / Volume 23 / Issue 1 / February 2013
- Published online by Cambridge University Press:
- 14 December 2012, pp. b1-b7
-
- Article
-
- You have access
- Export citation
Using the crowd for readability prediction
-
- Journal:
- Natural Language Engineering / Volume 20 / Issue 3 / July 2014
- Published online by Cambridge University Press:
- 14 December 2012, pp. 293-325
-
- Article
- Export citation
Using morphemes in language modeling and automatic speech recognition of Amharic
-
- Journal:
- Natural Language Engineering / Volume 20 / Issue 2 / April 2014
- Published online by Cambridge University Press:
- 12 December 2012, pp. 235-259
-
- Article
- Export citation
ON ORDERINGS BETWEEN WEIGHTED SUMS OF RANDOM VARIABLES
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 27 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 10 December 2012, pp. 85-97
-
- Article
- Export citation
THE SEQUENTIAL STOCHASTIC ASSIGNMENT PROBLEM WITH POSTPONEMENT OPTIONS
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 27 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 10 December 2012, pp. 25-51
-
- Article
- Export citation
ANALYTIC PROPERTIES OF TWO-CAROUSEL SYSTEMS
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 27 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 10 December 2012, pp. 57-84
-
- Article
- Export citation
A MARKOV CHAIN CHOICE PROBLEM
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 27 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 10 December 2012, pp. 53-55
-
- Article
- Export citation
Applications of the Semi-Definite Method to the Turán Density Problem for 3-Graphs
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. 21-54
-
- Article
- Export citation
CPC volume 22 issue 1 Cover and Front matter
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. f1-f2
-
- Article
-
- You have access
- Export citation
Improved Mixing Time Bounds for the Thorp Shuffle
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. 118-132
-
- Article
- Export citation
A Multipartite Version of the Hajnal–Szemerédi Theorem for Graphs and Hypergraphs
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. 97-111
-
- Article
- Export citation
CPC volume 22 issue 1 Cover and Back matter
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. b1-b4
-
- Article
-
- You have access
- Export citation
Preface
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 06 December 2012, pp. 1-2
- Print publication:
- January 2013
-
- Article
-
- You have access
- Export citation
JFP volume 23 issue 1 Cover and Front matter
-
- Journal:
- Journal of Functional Programming / Volume 23 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 05 December 2012, pp. f1-f2
-
- Article
-
- You have access
- Export citation

Data-Intensive Computing
- Architectures, Algorithms, and Applications
-
- Published online:
- 05 December 2012
- Print publication:
- 29 October 2012