Refine search
Actions for selected content:
48529 results in Computer Science
An intrinsically non minimal-time Minsky-like 6-states solution to the Firing Squad synchronization problem
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 42 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 18 January 2008, pp. 55-68
- Print publication:
- January 2008
-
- Article
- Export citation
Efficient execution in an automated reasoning environment
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 18 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 15-46
-
- Article
-
- You have access
- Export citation
Applicative programming with effects
-
- Journal:
- Journal of Functional Programming / Volume 18 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 1-13
-
- Article
-
- You have access
- Export citation
Enumerating Contingency Tables via Random Permanents
-
- Journal:
- Combinatorics, Probability and Computing / Volume 17 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 1-19
-
- Article
- Export citation
On Iterated Image Size for Point-Symmetric Relations
-
- Journal:
- Combinatorics, Probability and Computing / Volume 17 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 61-66
-
- Article
- Export citation
Calculating modules in contextual logic program refinement
-
- Journal:
- Theory and Practice of Logic Programming / Volume 8 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 1-31
-
- Article
- Export citation
Learning verb complements for Modern Greek: balancing the noisy dataset
-
- Journal:
- Natural Language Engineering / Volume 14 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 71-100
-
- Article
- Export citation
Learning discrete categorial grammars from structures
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 42 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 18 January 2008, pp. 165-182
- Print publication:
- January 2008
-
- Article
- Export citation
Enumeration Schemes for Restricted Permutations
-
- Journal:
- Combinatorics, Probability and Computing / Volume 17 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 137-159
-
- Article
- Export citation
Natural language processing in CLIME, a multilingual legal advisory system†
-
- Journal:
- Natural Language Engineering / Volume 14 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 101-132
-
- Article
- Export citation
An operational semantics for Scheme1
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 18 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 47-86
-
- Article
-
- You have access
- Export citation
Deciding whether a relation defined inPresburger logiccan be defined in weaker logics
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 42 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 18 January 2008, pp. 121-135
- Print publication:
- January 2008
-
- Article
- Export citation
Recurrence with affine level mappings is P-time decidable for CLP
-
- Journal:
- Theory and Practice of Logic Programming / Volume 8 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 111-119
-
- Article
- Export citation
Logic programming with satisfiability
-
- Journal:
- Theory and Practice of Logic Programming / Volume 8 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 121-128
-
- Article
- Export citation
The Critical Phase for Random Graphs with a Given Degree Sequence
-
- Journal:
- Combinatorics, Probability and Computing / Volume 17 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 67-86
-
- Article
- Export citation
Linear tabling strategies and optimizations
-
- Journal:
- Theory and Practice of Logic Programming / Volume 8 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 81-109
-
- Article
- Export citation
The Distribution of Patterns in Random Trees
-
- Journal:
- Combinatorics, Probability and Computing / Volume 17 / Issue 1 / January 2008
- Published online by Cambridge University Press:
- 01 January 2008, pp. 21-59
-
- Article
- Export citation
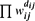 . For different choices of
. For different choices of 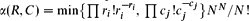 . In many cases, ln
. In many cases, ln 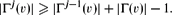
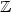
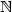
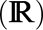
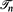 denote the set of unrooted labelled trees of size
denote the set of unrooted labelled trees of size 