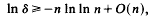Refine search
Actions for selected content:
9084 results in Discrete Mathematics, Information Theory and Coding
Transitive flows: a semi-group approach
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 348-361
- Print publication:
- December 1991
-
- Article
- Export citation
Conjugate points on convex surfaces
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 312-317
- Print publication:
- December 1991
-
- Article
- Export citation
On pairs of cubic Diophantine inequalities
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 250-263
- Print publication:
- December 1991
-
- Article
- Export citation
I. S. Barnett. Matrices: Methods and Applications. Clarendon Press. 1990, 450 pp., £17·50. - N. Boccara. Functional Analysis: An Introduction for Physicists. Academic Press. 1990, 327 pp., $44.50. - C. Canuto, M. Y. Hussaini, A. Quarteroni and T. A. Zang. Spectral Methods in Fluid Dynamics. Springer. 1988, 567 pp., DM 98. - G. Cherbit. Editor. Fractals; Non-integral Dimensions and Applications. Wiley. 1991, 249 pp., £29·95. - B. Choudhary and S. Nanda. Functional Analysis with Applications. Wiley. 1989, 344 pp., £27·80. - W. Dunham. Journey Through Genius―The Great Theorems of Mathematics. Wiley. 1990, 300 pp., £14·95. - A. Von Eye. Editor. Statistical Methods in Longitudinal Research. Volume I: Principles and Structuring Change. Volume II: Time Series and Categorical Longitudinal Data. Academic Press. 1990, 570 pp. in total, each volume $ 74.95. - S. O. Fatunla. Numerical Methods for Initial Value Problems in Ordinary Differential Equations. Academic Press. 1988, 295 pp., $44.50. - A. T. Fomenko. Variational Problems in Topology: The Geometry of Length, Area and Volume. Gordon and Breach. 1990, 225 pp., $120. - I. M. Gel'fand, M. I. Graev and I. I. Pyatetskii-Shapiro. Representation Theory and Automorphic Functions. Academic Press. 1990, 426 pp., paperback $39.50. - L. M. Hocking. Optimal Control: An Introduction to the Theory with Applications. Clarendon Press. 1991, 254 pp., £16. - S. S. Holland Jr Applied Analysis by the Hilbert Space Method. Marcel Dekker. 1990, 560 pp., $55. - D. F. Holt and W. Plesken. Perfect Groups. Clarendon Press. 1989, 376 pp., £35. - J. H. Hubbard and B. H. West. Differential Equations. A Dynamical Systems Approach. Part I. Springer. 1991, 348 pp., DM 78. - A. I. Kostrikin and Y. I. Manin. Linear Algebra and Geometry. Gordon and Breach. 1989, 309 pp., $270. - A. D. Linde. Inflation and Quantum Cosmology. Academic Press. 1990, 199 pp., $29.95. - M. Lunn. A First Course in Mechanics. Oxford. 1991, 192 pp., £12·95. - G. A. Margulis. Discrete Subgroups of Semisimple Lie Groups. Springer. 1991, 388 pp., DM 148. - S. M. Nikol'skii. Editor. Spaces of Differentiable Functions. Springer. 1991, 219 pp., DM 128. - F. Oberhettinger. Tables of Fourier Transforms and Fourier Transforms of Distributions. Springer. 1990, 259 pp., DM 64. - C. Parikh. The Unreal Life of Oscar Zariski. Academic Press. 1991, 264 pp. and 40 photographs, $32.95. - M. D. Potter. Sets: An Introduction. Clarendon Press. 1990, 241 pp., £15. - A. P. Prudnikov, Y. A. Brychkov and O. I. Marichev. Integrals and Series: Vol. 3, More Special Functions. Gordon and Breach. 1990, 800 pp., $175. - P. L. Sachdev. Nonlinear Ordinary Differential Equations and Their Applications. Marcel Dekker. 1991, 578 pp., $132. - S. S. Sritharan. Invariant Manifold Theory for Hydrodynamic Transition. Longman. 1990, 163 pp., £17·95. - G. J. Székely. Paradoxa: Klassische und neue Überraschungen aus Wahrscheinlichkeitsrechnung und mathematischer Statistik. Akadémiai Kiadó, Budapest. 1990, 240 pp., £15. - L. Ting and R. Klein. Viscous Vortical Flows. Springer. 1991, 222 pp., DM 42. - A. M. Vershik and D. P. Zhelobenko. Editors. Representation of Lie Groups and Related Topics. Gordon and Breach. 1990, 557 pp., $294.
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 398-404
- Print publication:
- December 1991
-
- Article
- Export citation
Oscillating viscous flows: II superposed oscillations
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 203-216
- Print publication:
- December 1991
-
- Article
- Export citation
Prolongations of valuations to simple transcendental extensions with given residue field and value group
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 386-390
- Print publication:
- December 1991
-
- Article
- Export citation
Small solutions of quadratic congruences, II
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 264-284
- Print publication:
- December 1991
-
- Article
- Export citation
MTK volume 38 issue 2 Cover and Front matter
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. f1-f2
- Print publication:
- December 1991
-
- Article
-
- You have access
- Export citation
Measures in banach spaces are determined by their values on balls
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 391-397
- Print publication:
- December 1991
-
- Article
- Export citation
Coefficient functions for an inhomogeneous turning-point problem
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 217-238
- Print publication:
- December 1991
-
- Article
- Export citation
Upper and lower bound results on the convex hull of integer points in polyhedra
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 321-328
- Print publication:
- December 1991
-
- Article
- Export citation
Covering squares with independent squares
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 329-333
- Print publication:
- December 1991
-
- Article
- Export citation
Lonely knots and tangles: Identifying knots with no companions
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 334-347
- Print publication:
- December 1991
-
- Article
- Export citation
Index to volume 38
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, p. 405
- Print publication:
- December 1991
-
- Article
- Export citation
Limit points of partial sums of Taylor series
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 239-249
- Print publication:
- December 1991
-
- Article
- Export citation
The problem of illumination of the boundary of a convex body by affine subspaces
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 362-375
- Print publication:
- December 1991
-
- Article
- Export citation
Value groups and simple transcendental extensions
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 381-385
- Print publication:
- December 1991
-
- Article
- Export citation
Contact structures on 1-connected 5-manifolds
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 303-311
- Print publication:
- December 1991
-
- Article
- Export citation
An ellipsoid packing in E3 of unexpected high density
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 318-320
- Print publication:
- December 1991
-
- Article
- Export citation
Constructive packings of cross polytopes
- Part of
-
- Journal:
- Mathematika / Volume 38 / Issue 2 / December 1991
- Published online by Cambridge University Press:
- 26 February 2010, pp. 376-380
- Print publication:
- December 1991
-
- Article
- Export citation
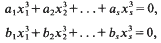
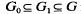 is an inclusion of totally ordered abelian groups with [
is an inclusion of totally ordered abelian groups with [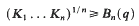
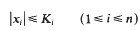
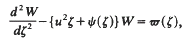
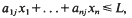 for
for 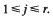 The maximum is necessarily attained at one of the vertices of the convex hull of integer points defined by the inequalities, so we have an interest in estimating the number
The maximum is necessarily attained at one of the vertices of the convex hull of integer points defined by the inequalities, so we have an interest in estimating the number