Refine search
Actions for selected content:
6974 results in Algorithmics, Complexity, Computer Algebra, Computational Geometry
Some results on complexity of μ-calculusevaluation in the black-box model∗
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 10 January 2013, pp. 97-109
- Print publication:
- January 2013
-
- Article
- Export citation
Strong functors and interleaving fixpoints in gamesemantics∗
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 10 January 2013, pp. 25-68
- Print publication:
- January 2013
-
- Article
- Export citation
A non-uniform finitary relational semantics of systemT∗
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 10 January 2013, pp. 111-132
- Print publication:
- January 2013
-
- Article
- Export citation
Avoiding Arrays of Odd Order by Latin Squares
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 2 / March 2013
- Published online by Cambridge University Press:
- 21 December 2012, pp. 184-212
-
- Article
- Export citation
Asymptotic Normality Through Factorial Cumulants and Partition Identities
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 2 / March 2013
- Published online by Cambridge University Press:
- 21 December 2012, pp. 213-240
-
- Article
- Export citation
Optimal Packings of Hamilton Cycles in Graphs of High Minimum Degree
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 3 / May 2013
- Published online by Cambridge University Press:
- 20 December 2012, pp. 394-416
-
- Article
- Export citation
On Core XPath with Inflationary Fixed Points∗
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 19 December 2012, pp. 3-23
- Print publication:
- January 2013
-
- Article
- Export citation
Applications of the Semi-Definite Method to the Turán Density Problem for 3-Graphs
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. 21-54
-
- Article
- Export citation
CPC volume 22 issue 1 Cover and Front matter
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. f1-f2
-
- Article
-
- You have access
- Export citation
Improved Mixing Time Bounds for the Thorp Shuffle
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. 118-132
-
- Article
- Export citation
A Multipartite Version of the Hajnal–Szemerédi Theorem for Graphs and Hypergraphs
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. 97-111
-
- Article
- Export citation
CPC volume 22 issue 1 Cover and Back matter
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 07 December 2012, pp. b1-b4
-
- Article
-
- You have access
- Export citation
Preface
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 06 December 2012, pp. 1-2
- Print publication:
- January 2013
-
- Article
-
- You have access
- Export citation
A tight bound for exhaustive key search attacks against MessageAuthentication Codes
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 2 / April 2013
- Published online by Cambridge University Press:
- 06 November 2012, pp. 171-180
- Print publication:
- April 2013
-
- Article
- Export citation
On the hardness of game equivalence under localisomorphism∗
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 2 / April 2013
- Published online by Cambridge University Press:
- 05 November 2012, pp. 147-169
- Print publication:
- April 2013
-
- Article
- Export citation
Signed Chip Firing Games and symmetric Sandpile Models on thecycles∗
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 47 / Issue 2 / April 2013
- Published online by Cambridge University Press:
- 31 October 2012, pp. 133-146
- Print publication:
- April 2013
-
- Article
- Export citation
Sums of Dilates in
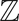 p
p
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 2 / March 2013
- Published online by Cambridge University Press:
- 30 October 2012, pp. 282-293
-
- Article
- Export citation
The Largest Minimum Codegree of a 3-Graph Without a Generalized 4-Cycle
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 19 October 2012, pp. 112-117
-
- Article
- Export citation
Hypergraph Independent Sets
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 11 October 2012, pp. 9-20
-
- Article
- Export citation
Probably Intersecting Families are Not Nested
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 1 / January 2013
- Published online by Cambridge University Press:
- 09 October 2012, pp. 146-160
-
- Article
- Export citation