Refine search
Actions for selected content:
48585 results in Computer Science
STOCHASTIC ORDER OF SAMPLE RANGE FROM HETEROGENEOUS EXPONENTIAL RANDOM VARIABLES
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 23 / Issue 1 / January 2009
- Published online by Cambridge University Press:
- 13 November 2008, pp. 17-29
-
- Article
- Export citation
PERFORMANCE ESTIMATION OF M/DK/1 QUEUE UNDER FAIR SOJOURN PROTOCOL IN HEAVY TRAFFIC
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 23 / Issue 1 / January 2009
- Published online by Cambridge University Press:
- 13 November 2008, pp. 61-74
-
- Article
- Export citation
DYNAMIC ROUTING POLICIES FOR MULTISKILL CALL CENTERS
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 23 / Issue 1 / January 2009
- Published online by Cambridge University Press:
- 13 November 2008, pp. 101-119
-
- Article
- Export citation
HITTING PROBABILITIES AND HITTING TIMES FOR STOCHASTIC FLUID FLOWS: THE BOUNDED MODEL
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 23 / Issue 1 / January 2009
- Published online by Cambridge University Press:
- 13 November 2008, pp. 121-147
-
- Article
- Export citation
PROPORTIONAL THREE-PERSON RED-AND-BLACK GAMES
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 23 / Issue 1 / January 2009
- Published online by Cambridge University Press:
- 13 November 2008, pp. 37-50
-
- Article
- Export citation
Author Index to Volume 2
-
- Journal:
- Journal of Functional Programming / Volume 2 / Issue 4 / October 1992
- Published online by Cambridge University Press:
- 07 November 2008, p. 515
-
- Article
-
- You have access
- Export citation
Principal signatures for higher-order program modules
-
- Journal:
- Journal of Functional Programming / Volume 4 / Issue 3 / July 1994
- Published online by Cambridge University Press:
- 07 November 2008, pp. 285-335
-
- Article
-
- You have access
- Export citation
The virtues of eta-expansion
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 5 / Issue 2 / April 1995
- Published online by Cambridge University Press:
- 07 November 2008, pp. 135-154
-
- Article
-
- You have access
- Export citation
Functional Pearls: Unravelling greedy algorithms
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 2 / Issue 3 / July 1992
- Published online by Cambridge University Press:
- 07 November 2008, pp. 375-385
-
- Article
-
- You have access
- Export citation
Functional Pearls: Deriving tidy drawings of trees
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 6 / Issue 3 / May 1996
- Published online by Cambridge University Press:
- 07 November 2008, pp. 535-562
-
- Article
-
- You have access
- Export citation
Theoretical Pearls Enumerators of lambda terms are reducing
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 2 / Issue 2 / April 1992
- Published online by Cambridge University Press:
- 07 November 2008, pp. 233-236
-
- Article
-
- You have access
- Export citation
An Introduction to Formal Specification and Z by Ben Potter, Jane Sinclair and David Till, Prentice-Hall, 1991. - Z: An Introduction to Formal Methods (second edition) by Antoni Diller, John Wiley & Sons, 1994.
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 6 / Issue 2 / March 1996
- Published online by Cambridge University Press:
- 07 November 2008, pp. 375-377
-
- Article
-
- You have access
- Export citation
Defining data structures via Böhm-out1
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 5 / Issue 1 / January 1995
- Published online by Cambridge University Press:
- 07 November 2008, pp. 51-64
-
- Article
-
- You have access
- Export citation
Program transformation with metasystem transitions
- Part of
-
- Journal:
- Journal of Functional Programming / Volume 3 / Issue 3 / July 1993
- Published online by Cambridge University Press:
- 07 November 2008, pp. 283-313
-
- Article
-
- You have access
- Export citation
JFP volume 5 issue 1 Cover and Back matter
-
- Journal:
- Journal of Functional Programming / Volume 5 / Issue 1 / January 1995
- Published online by Cambridge University Press:
- 07 November 2008, pp. b1-b2
-
- Article
-
- You have access
- Export citation
A partial evaluator for the untyped lambda-calculus
-
- Journal:
- Journal of Functional Programming / Volume 1 / Issue 1 / January 1991
- Published online by Cambridge University Press:
- 07 November 2008, pp. 21-69
-
- Article
-
- You have access
- Export citation
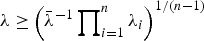 with
with 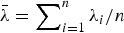 . Further, this usual stochastic order is strengthened to the hazard rate order for
. Further, this usual stochastic order is strengthened to the hazard rate order for