Refine search
Actions for selected content:
9084 results in Discrete Mathematics, Information Theory and Coding
Reconstruction of polytopes by convex pastings
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 9-18
- Print publication:
- December 2000
-
- Article
- Export citation
Scattering of tidal waves by reefs and spits
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 355-370
- Print publication:
- December 2000
-
- Article
- Export citation
Maximal sections and centrally symmetric bodies
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 19-30
- Print publication:
- December 2000
-
- Article
- Export citation
Inscribing cubes and covering by rhombic dodecahedra via equivariant topology
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 371-397
- Print publication:
- December 2000
-
- Article
- Export citation
Combinatorics and linear algebra of Freiman's isomorphism
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 39-51
- Print publication:
- December 2000
-
- Article
- Export citation
Lusternik-Schnirelmann category and Morse decompositions
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 299-305
- Print publication:
- December 2000
-
- Article
- Export citation
Frequency of oscillations of an error term related to the Euler function
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 161-164
- Print publication:
- December 2000
-
- Article
- Export citation
A functional analytic interpretation of the number of faces of a polyhedron
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 1-7
- Print publication:
- December 2000
-
- Article
- Export citation
Factorization over local fields and the irreducibility of generalized difference polynomials
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 173-196
- Print publication:
- December 2000
-
- Article
- Export citation
Un nouveau critère pour l'équation de Catalan
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 63-73
- Print publication:
- December 2000
-
- Article
- Export citation
The discrete fractional Fourier transform and Harper's equation
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 281-297
- Print publication:
- December 2000
-
- Article
- Export citation
Bounds for the points of spectral concentration of Sturm–Liouville problems
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 327-337
- Print publication:
- December 2000
-
- Article
- Export citation
The convexity of the spectral function in Sturm–Liouville problems
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 319-326
- Print publication:
- December 2000
-
- Article
- Export citation
N-fold sums of Cantor sets
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 243-250
- Print publication:
- December 2000
-
- Article
- Export citation
Character sums with exponential functions
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 75-85
- Print publication:
- December 2000
-
- Article
- Export citation
The order of inverses mod q
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 87-108
- Print publication:
- December 2000
-
- Article
- Export citation
Index to volume 47
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 411-412
- Print publication:
- December 2000
-
- Article
- Export citation
The order of groups satisfying a converse to Lagrange's theorem
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 197-204
- Print publication:
- December 2000
-
- Article
- Export citation
On properties of metrizable spaces X preserved by t-equivalence
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 273-279
- Print publication:
- December 2000
-
- Article
- Export citation
Density and covering properties of intervals of ℝn
- Part of
-
- Journal:
- Mathematika / Volume 47 / Issue 1-2 / December 2000
- Published online by Cambridge University Press:
- 26 February 2010, pp. 229-242
- Print publication:
- December 2000
-
- Article
- Export citation
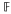 of convex sets, satisfying a given property P. Moreover, assume that
of convex sets, satisfying a given property P. Moreover, assume that 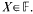 . As a consequence, it follows that, if all simplices or small enough simplices have the property in question, then
. As a consequence, it follows that, if all simplices or small enough simplices have the property in question, then  of classes of such cardinality
of classes of such cardinality 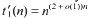 .
.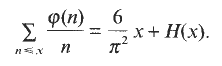
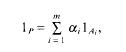


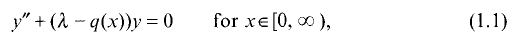
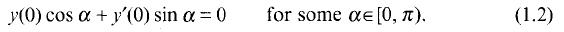
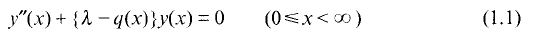
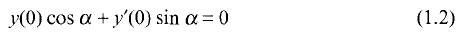
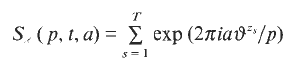
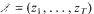 a sequence such that
a sequence such that 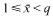 be such that
be such that 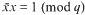 . For fixed
. For fixed 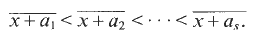
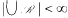 , then there is a finite sequence
, then there is a finite sequence 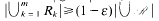 and
and 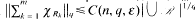 .
.