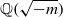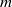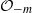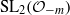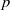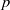Refine search
Actions for selected content:
48202 results in Computer Science
4 - Further Topics from Information Theory
-
- Book:
- Information Theory and Coding by Example
- Published online:
- 05 June 2014
- Print publication:
- 12 September 2013, pp 366-500
-
- Chapter
- Export citation
Network analysis of narrative content in large corpora
-
- Journal:
- Natural Language Engineering / Volume 21 / Issue 1 / January 2015
- Published online by Cambridge University Press:
- 11 September 2013, pp. 81-112
-
- Article
- Export citation
Commentary: Teach network science to teenagers
-
- Journal:
- Network Science / Volume 1 / Issue 2 / August 2013
- Published online by Cambridge University Press:
- 10 September 2013, pp. 226-247
-
- Article
- Export citation
Classifying Korean comparative sentences for comparison analysis
-
- Journal:
- Natural Language Engineering / Volume 20 / Issue 4 / October 2014
- Published online by Cambridge University Press:
- 09 September 2013, pp. 557-581
-
- Article
- Export citation
SePaS: Word sense disambiguation by sequential patterns in sentences
-
- Journal:
- Natural Language Engineering / Volume 21 / Issue 2 / March 2015
- Published online by Cambridge University Press:
- 06 September 2013, pp. 251-269
-
- Article
- Export citation
Improving syntactic rule extraction through deleting spurious links with translation span alignment
-
- Journal:
- Natural Language Engineering / Volume 21 / Issue 2 / March 2015
- Published online by Cambridge University Press:
- 06 September 2013, pp. 227-249
-
- Article
- Export citation
A survey of different approaches to support in argumentation systems
-
- Journal:
- The Knowledge Engineering Review / Volume 29 / Issue 5 / November 2014
- Published online by Cambridge University Press:
- 05 September 2013, pp. 513-550
-
- Article
- Export citation

Elements of Automata Theory
-
- Published online:
- 05 September 2013
- Print publication:
- 01 October 2009

The Handbook of Personal Area Networking Technologies and Protocols
-
- Published online:
- 05 September 2013
- Print publication:
- 29 August 2013

Memory Machines
- The Evolution of Hypertext
-
- Published by:
- Anthem Press
- Published online:
- 05 September 2013
- Print publication:
- 15 July 2013

Sets and Proofs
-
- Published online:
- 05 September 2013
- Print publication:
- 17 June 1999
Relative Tutte Polynomials of Tensor Products of Coloured Graphs
-
- Journal:
- Combinatorics, Probability and Computing / Volume 22 / Issue 6 / November 2013
- Published online by Cambridge University Press:
- 04 September 2013, pp. 801-828
-
- Article
- Export citation
Planning in BDI agents: a survey of the integration of planning algorithms and agent reasoning
-
- Journal:
- The Knowledge Engineering Review / Volume 30 / Issue 1 / January 2015
- Published online by Cambridge University Press:
- 04 September 2013, pp. 1-44
-
- Article
-
- You have access
- HTML
- Export citation
Weak approximation of stochastic differential delay equations for bounded measurable function
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 16 / October 2013
- Published online by Cambridge University Press:
- 01 September 2013, pp. 319-343
-
- Article
-
- You have access
- Export citation
Corrigendum: On the use of a discrete form of the Itô formula in the article ‘Almost sure asymptotic stability analysis of the
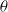 $\theta $ -Maruyama method applied to a test system with stabilising and destabilising stochastic perturbations’
$\theta $ -Maruyama method applied to a test system with stabilising and destabilising stochastic perturbations’
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 16 / October 2013
- Published online by Cambridge University Press:
- 01 September 2013, pp. 366-372
-
- Article
-
- You have access
- Export citation
Higher torsion in the Abelianization of the full Bianchi groups
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 16 / October 2013
- Published online by Cambridge University Press:
- 01 September 2013, pp. 344-365
-
- Article
-
- You have access
- Export citation