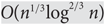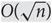Refine search
Actions for selected content:
48287 results in Computer Science
Surjectivity of near-square random matrices
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 2 / March 2020
- Published online by Cambridge University Press:
- 06 November 2019, pp. 267-292
-
- Article
- Export citation
Using fMRI to deepen our understanding of design fixation
- Part of
-
- Journal:
- Design Science / Volume 5 / 2019
- Published online by Cambridge University Press:
- 06 November 2019, e22
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Team learning from human demonstration with coordination confidence
- Part of
-
- Journal:
- The Knowledge Engineering Review / Volume 34 / 2019
- Published online by Cambridge University Press:
- 05 November 2019, e12
-
- Article
- Export citation
Assessing the stability of egocentric networks over time using the digital participant-aided sociogram tool Network Canvas
-
- Journal:
- Network Science / Volume 8 / Issue 2 / June 2020
- Published online by Cambridge University Press:
- 04 November 2019, pp. 204-222
-
- Article
-
- You have access
- Open access
- Export citation
Structure in personal networks: Constructing and comparing typologies
-
- Journal:
- Network Science / Volume 8 / Issue 2 / June 2020
- Published online by Cambridge University Press:
- 04 November 2019, pp. 142-167
-
- Article
- Export citation
The networked question in the digital era: How do networked, bounded, and limited individuals connect at different stages in the life course?
-
- Journal:
- Network Science / Volume 8 / Issue 3 / September 2020
- Published online by Cambridge University Press:
- 04 November 2019, pp. 291-312
-
- Article
- Export citation
A LEARNING-THEORETIC CHARACTERISATION OF MARTIN-LÖF RANDOMNESS AND SCHNORR RANDOMNESS
- Part of
-
- Journal:
- The Review of Symbolic Logic / Volume 14 / Issue 2 / June 2021
- Published online by Cambridge University Press:
- 04 November 2019, pp. 531-549
- Print publication:
- June 2021
-
- Article
- Export citation
The embeddedness of social capital in personal networks
-
- Journal:
- Network Science / Volume 8 / Issue 2 / June 2020
- Published online by Cambridge University Press:
- 04 November 2019, pp. 189-203
-
- Article
- Export citation
The string of diamonds is nearly tight for rumour spreading
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 2 / March 2020
- Published online by Cambridge University Press:
- 04 November 2019, pp. 190-199
-
- Article
- Export citation
Unlabelled Gibbs partitions
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 2 / March 2020
- Published online by Cambridge University Press:
- 04 November 2019, pp. 293-309
-
- Article
- Export citation
Friendship networks and adolescent pregnancy: Examining the potential stigmatization of pregnant teens
-
- Journal:
- Network Science / Volume 7 / Issue 4 / December 2019
- Published online by Cambridge University Press:
- 04 November 2019, pp. 523-540
-
- Article
- Export citation
Survey on Aerial Manipulator: System, Modeling, and Control
-
- Article
-
- You have access
- Export citation
Contents
-
- Book:
- Getting In and Getting On in the Youth Labour Market
- Published by:
- Bristol University Press
- Published online:
- 10 March 2021
- Print publication:
- 29 October 2019, pp v-v
-
- Chapter
- Export citation
Three - Enterprise on the South Coast
-
- Book:
- Getting In and Getting On in the Youth Labour Market
- Published by:
- Bristol University Press
- Published online:
- 10 March 2021
- Print publication:
- 29 October 2019, pp 55-82
-
- Chapter
- Export citation