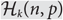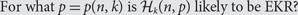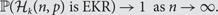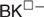Refine search
Actions for selected content:
48196 results in Computer Science
Acknowledgements
-
- Book:
- Game Theory for Next Generation Wireless and Communication Networks
- Published online:
- 13 June 2019
- Print publication:
- 27 June 2019, pp xii-xii
-
- Chapter
- Export citation
11 - Applications of Game Theory in Cloud Networking
- from Part II - Applications
-
- Book:
- Game Theory for Next Generation Wireless and Communication Networks
- Published online:
- 13 June 2019
- Print publication:
- 27 June 2019, pp 270-314
-
- Chapter
- Export citation
PERFORMANCE MEASURES FOR THE TWO-NODE QUEUE WITH FINITE BUFFERS
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 34 / Issue 4 / October 2020
- Published online by Cambridge University Press:
- 26 June 2019, pp. 522-549
-
- Article
- Export citation
On Erdős–Ko–Rado for random hypergraphs I
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 28 / Issue 6 / November 2019
- Published online by Cambridge University Press:
- 25 June 2019, pp. 881-916
-
- Article
- Export citation

Variational Bayesian Learning Theory
-
- Published online:
- 24 June 2019
- Print publication:
- 11 July 2019

Lawless
- The Secret Rules That Govern our Digital Lives
-
- Published online:
- 22 June 2019
- Print publication:
- 18 July 2019
A Logic Framework for P2P Deductive Databases
-
- Journal:
- Theory and Practice of Logic Programming / Volume 20 / Issue 1 / January 2020
- Published online by Cambridge University Press:
- 19 June 2019, pp. 1-43
-
- Article
- Export citation
PROOF SYSTEMS FOR VARIOUS FDE-BASED MODAL LOGICS
-
- Journal:
- The Review of Symbolic Logic / Volume 13 / Issue 4 / December 2020
- Published online by Cambridge University Press:
- 17 June 2019, pp. 720-747
- Print publication:
- December 2020
-
- Article
- Export citation