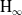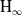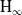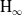Refine search
Actions for selected content:
48569 results in Computer Science
A generalization of Bondy’s pancyclicity theorem
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 33 / Issue 5 / September 2024
- Published online by Cambridge University Press:
- 17 April 2024, pp. 554-563
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Unleashing collective intelligence for public decision-making: the Data for Policy community
-
- Journal:
- Data & Policy / Volume 6 / 2024
- Published online by Cambridge University Press:
- 15 April 2024, e23
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
3 - Fair Is Lovely; Boys Will Be Boys: Notes on Gender, Class, and Technologies
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 61-98
-
- Chapter
- Export citation
Frontmatter
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 1-4
-
- Chapter
- Export citation
About the Author
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 177-178
-
- Chapter
- Export citation
5 - Digital Traces of Religious Identities: On Belongingness and Anxiety
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 137-168
-
- Chapter
- Export citation
A 2-categorical proof of Frobenius for fibrations defined from a generic point
-
- Journal:
- Mathematical Structures in Computer Science / Volume 34 / Issue 4 / April 2024
- Published online by Cambridge University Press:
- 15 April 2024, pp. 258-280
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
1 - Introduction
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 9-38
-
- Chapter
- Export citation
4 - (Non)Negotiating Caste in Digital Encounters
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 99-136
-
- Chapter
- Export citation
Contents
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 7-8
-
- Chapter
- Export citation
Frequency-dependent
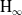 $\textrm{H}_{{\infty }}$ control for wind disturbance rejection of a fully actuated UAV
$\textrm{H}_{{\infty }}$ control for wind disturbance rejection of a fully actuated UAV
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
6 - Inhabiting a Digital Dystopia?
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 169-176
-
- Chapter
- Export citation
Index
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 179-180
-
- Chapter
- Export citation
Dedication
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 5-6
-
- Chapter
- Export citation
2 - Living in a Technological Utopia
-
- Book:
- Children's Digital Experiences in Indian Slums
- Published by:
- Amsterdam University Press
- Published online:
- 18 December 2024
- Print publication:
- 15 April 2024, pp 39-60
-
- Chapter
- Export citation
Empirical evidence and computational assessment on design knowledge transferability
-
- Journal:
- Design Science / Volume 10 / 2024
- Published online by Cambridge University Press:
- 12 April 2024, e10
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
When can networks be inferred from observed groups?
-
- Journal:
- Network Science / Volume 12 / Issue 2 / June 2024
- Published online by Cambridge University Press:
- 12 April 2024, pp. 189-200
-
- Article
-
- You have access
- Open access
- HTML
- Export citation