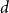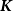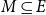Refine search
Actions for selected content:
48569 results in Computer Science
Turán problems in pseudorandom graphs
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 33 / Issue 5 / September 2024
- Published online by Cambridge University Press:
- 29 April 2024, pp. 583-596
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Open data, workplace relations law compliance, and digital regulation
-
- Journal:
- Data & Policy / Volume 6 / 2024
- Published online by Cambridge University Press:
- 29 April 2024, e26
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Central limit theorem for components in meandric systems through high moments
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 33 / Issue 5 / September 2024
- Published online by Cambridge University Press:
- 29 April 2024, pp. 597-610
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
The latent cognitive structures of social networks
-
- Journal:
- Network Science / Volume 12 / Issue 3 / September 2024
- Published online by Cambridge University Press:
- 25 April 2024, pp. 202-233
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
An inequality for log-concave functions and its use in the study of failure rates
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 38 / Issue 4 / October 2024
- Published online by Cambridge University Press:
- 23 April 2024, pp. 695-704
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Behaviour of the minimum degree throughout the
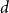 ${\textit{d}}$-process
${\textit{d}}$-process
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 33 / Issue 5 / September 2024
- Published online by Cambridge University Press:
- 22 April 2024, pp. 564-582
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
You can only be lucky once: optimal gossip for epistemic goals
-
- Journal:
- Mathematical Structures in Computer Science / Volume 34 / Issue 7 / August 2024
- Published online by Cambridge University Press:
- 19 April 2024, pp. 661-688
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Exploring the practices of “data-driven innovation” in the European public sector
-
- Journal:
- Data & Policy / Volume 6 / 2024
- Published online by Cambridge University Press:
- 19 April 2024, e24
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Radial basis function neural networks for formation control of unmanned aerial vehicles
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Abstract cyclic proofs
-
- Journal:
- Mathematical Structures in Computer Science / Volume 34 / Issue 7 / August 2024
- Published online by Cambridge University Press:
- 19 April 2024, pp. 552-577
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
The innovation paradox: concept space expansion with diminishing originality and the promise of creative artificial intelligence
-
- Journal:
- Design Science / Volume 10 / 2024
- Published online by Cambridge University Press:
- 19 April 2024, e11
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
A granular examination of gender and racial disparities in federal procurement
-
- Journal:
- Data & Policy / Volume 6 / 2024
- Published online by Cambridge University Press:
- 19 April 2024, e25
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Discounted cost exponential semi-Markov decision processes with unbounded transition rates: a service rate control problem with impatient customers
-
- Journal:
- Probability in the Engineering and Informational Sciences / Volume 38 / Issue 4 / October 2024
- Published online by Cambridge University Press:
- 18 April 2024, pp. 668-694
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
New and improved bounds on the contextuality degree of multi-qubit configurations
-
- Journal:
- Mathematical Structures in Computer Science / Volume 34 / Issue 4 / April 2024
- Published online by Cambridge University Press:
- 18 April 2024, pp. 322-343
-
- Article
- Export citation
Equational theorem proving for clauses over strings
-
- Journal:
- Mathematical Structures in Computer Science / Volume 34 / Issue 10 / November 2024
- Published online by Cambridge University Press:
- 18 April 2024, pp. 1055-1078
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
An approximation algorithm for the
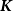 $\boldsymbol{K}$-prize-collecting multicut problem in trees with submodular penalties
$\boldsymbol{K}$-prize-collecting multicut problem in trees with submodular penalties
-
- Journal:
- Mathematical Structures in Computer Science / Volume 34 / Issue 3 / March 2024
- Published online by Cambridge University Press:
- 17 April 2024, pp. 193-210
-
- Article
- Export citation