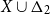Refine search
Actions for selected content:
48287 results in Computer Science
Some representations of real numbers using integer sequences
-
- Journal:
- Mathematical Structures in Computer Science / Volume 32 / Issue 5 / May 2022
- Published online by Cambridge University Press:
- 14 October 2022, pp. 648-681
-
- Article
- Export citation
An algebraic representation of the fixed-point closure of *-continuous Kleene algebras – A categorical Chomsky–Schützenberger theorem
-
- Journal:
- Mathematical Structures in Computer Science / Volume 32 / Issue 6 / June 2022
- Published online by Cambridge University Press:
- 14 October 2022, pp. 685-728
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Know Your Customer: Balancing innovation and regulation for financial inclusion
-
- Journal:
- Data & Policy / Volume 4 / 2022
- Published online by Cambridge University Press:
- 14 October 2022, e34
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Complete algebraic semantics for second-order rewriting systems based on abstract syntax with variable binding
-
- Journal:
- Mathematical Structures in Computer Science / Volume 32 / Issue 4 / April 2022
- Published online by Cambridge University Press:
- 14 October 2022, pp. 542-573
-
- Article
- Export citation
4 - Lists and Patterns
- from Part I - Language Concepts
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 50-65
-
- Chapter
-
- You have access
- Open access
- Export citation
23 - Foreign Function Interface
- from Part III - The Complier and Runtime System
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 405-423
-
- Chapter
-
- You have access
- Open access
- Export citation
3 - Variables and Functions
- from Part I - Language Concepts
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 31-49
-
- Chapter
-
- You have access
- Open access
- Export citation
17 - Concurrent Programming with Async
- from Part II - Tools and Techniques
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 297-324
-
- Chapter
-
- You have access
- Open access
- Export citation
25 - Understanding the Garbage Collector
- from Part III - The Complier and Runtime System
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 435-446
-
- Chapter
-
- You have access
- Open access
- Export citation
7 - Variants
- from Part I - Language Concepts
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 99-118
-
- Chapter
-
- You have access
- Open access
- Export citation
1 - Prologue
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 1-6
-
- Chapter
-
- You have access
- Open access
- Export citation
9 - Imperative Programming
- from Part I - Language Concepts
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 134-165
-
- Chapter
-
- You have access
- Open access
- Export citation
8 - Error Handling
- from Part I - Language Concepts
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 119-133
-
- Chapter
-
- You have access
- Open access
- Export citation
2 - A Guided Tour
- from Part I - Language Concepts
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 9-30
-
- Chapter
-
- You have access
- Open access
- Export citation
24 - Memory Representation of Values
- from Part III - The Complier and Runtime System
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 424-434
-
- Chapter
-
- You have access
- Open access
- Export citation
20 - Parsing with OCamllex and Menhir
- from Part II - Tools and Techniques
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 361-373
-
- Chapter
-
- You have access
- Open access
- Export citation
16 - Command-Line Parsing
- from Part II - Tools and Techniques
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 280-296
-
- Chapter
-
- You have access
- Open access
- Export citation
14 - Classes
- from Part I - Language Concepts
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 237-260
-
- Chapter
-
- You have access
- Open access
- Export citation
5 - Files, Modules, and Programs
- from Part I - Language Concepts
-
- Book:
- Real World OCaml: Functional Programming for the Masses
- Published online:
- 22 September 2022
- Print publication:
- 13 October 2022, pp 66-84
-
- Chapter
-
- You have access
- Open access
- Export citation