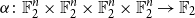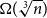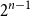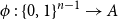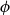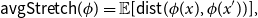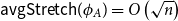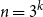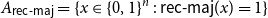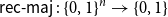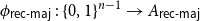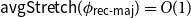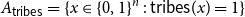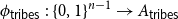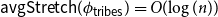Refine search
Actions for selected content:
48289 results in Computer Science
Chapter 20 - Concluding Thoughts
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp 265-277
-
- Chapter
- Export citation
Part IV - Addressing Concerns
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp 229-264
-
- Chapter
- Export citation
Chapter 11 - Understandability
- from Part III - Challenges in Applying Data Science
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp 154-186
-
- Chapter
- Export citation
References
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp 282-305
-
- Chapter
- Export citation
Chapter 1 - Foundations of Data Science
- from Part I - Data Science
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp 7-28
-
- Chapter
- Export citation
Chapter 9 - Building and Deploying Models
- from Part III - Challenges in Applying Data Science
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp 118-125
-
- Chapter
- Export citation
Recap of Part I: Data Science
- from Part I - Data Science
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp 41-44
-
- Chapter
- Export citation
Tables
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp xi-xii
-
- Chapter
- Export citation
Appendix - Summary of Recommendations from Part IV
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp 278-279
-
- Chapter
- Export citation
Part III - Challenges in Applying Data Science
-
- Book:
- Data Science in Context
- Published online:
- 29 September 2022
- Print publication:
- 20 October 2022, pp 109-228
-
- Chapter
- Export citation
An Application of a Runtime Epistemic Probabilistic Event Calculus to Decision-making in e-Health Systems
-
- Journal:
- Theory and Practice of Logic Programming / Volume 23 / Issue 5 / September 2023
- Published online by Cambridge University Press:
- 20 October 2022, pp. 1070-1093
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Identifying and minimising the impact of fake visual media: Current and future directions
- Part of
-
- Journal:
- Memory, Mind & Media / Volume 1 / 2022
- Published online by Cambridge University Press:
- 20 October 2022, e15
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Observing non-uniform, non-Lüders yielding in a cold-rolled medium manganese steel with digital image correlation
-
- Journal:
- Experimental Results / Volume 3 / 2022
- Published online by Cambridge University Press:
- 19 October 2022, e23
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Socio-spatial aspects of creativity and their role in the planning and design of university campuses’ public spaces: A practitioners’ perspective
-
- Journal:
- Data & Policy / Volume 4 / 2022
- Published online by Cambridge University Press:
- 18 October 2022, e35
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Approximately symmetric forms far from being exactly symmetric
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 32 / Issue 2 / March 2023
- Published online by Cambridge University Press:
- 18 October 2022, pp. 299-315
-
- Article
- Export citation
On mappings on the hypercube with small average stretch
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 32 / Issue 2 / March 2023
- Published online by Cambridge University Press:
- 18 October 2022, pp. 334-348
-
- Article
- Export citation
The Collection of Papers Celebrating the 20th Anniversary of TPLP, Part II
-
- Journal:
- Theory and Practice of Logic Programming / Volume 23 / Issue 1 / January 2023
- Published online by Cambridge University Press:
- 18 October 2022, p. 1
-
- Article
-
- You have access
- HTML
- Export citation
Preserving consistency in geometric modeling with graph transformations
-
- Journal:
- Mathematical Structures in Computer Science / Volume 32 / Issue 3 / March 2022
- Published online by Cambridge University Press:
- 18 October 2022, pp. 300-347
-
- Article
- Export citation
A benchmark for evaluating Arabic word embedding models
-
- Journal:
- Natural Language Engineering / Volume 29 / Issue 4 / July 2023
- Published online by Cambridge University Press:
- 17 October 2022, pp. 978-1003
-
- Article
- Export citation
High-resolution tropical rain-forest canopy climate data
-
- Journal:
- Environmental Data Science / Volume 1 / 2022
- Published online by Cambridge University Press:
- 17 October 2022, e13
-
- Article
-
- You have access
- Open access
- HTML
- Export citation