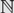Refine search
Actions for selected content:
48285 results in Computer Science
5 - Sparsity-Based Methods for CFAR Target Detection in STAP Random Arrays
-
- Book:
- Compressed Sensing in Radar Signal Processing
- Published online:
- 30 September 2019
- Print publication:
- 17 October 2019, pp 135-164
-
- Chapter
- Export citation
2 - Clutter Rejection and Adaptive Filtering in Compressed Sensing Radar
-
- Book:
- Compressed Sensing in Radar Signal Processing
- Published online:
- 30 September 2019
- Print publication:
- 17 October 2019, pp 49-71
-
- Chapter
- Export citation
List of Contributors
-
- Book:
- Compressed Sensing in Radar Signal Processing
- Published online:
- 30 September 2019
- Print publication:
- 17 October 2019, pp xi-xiii
-
- Chapter
- Export citation
A representation of proper BC domains based on conjunctive sequent calculi
-
- Journal:
- Mathematical Structures in Computer Science / Volume 30 / Issue 1 / January 2020
- Published online by Cambridge University Press:
- 16 October 2019, pp. 1-13
-
- Article
- Export citation
The Infinite limit of random permutations avoiding patterns of length three
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 1 / January 2020
- Published online by Cambridge University Press:
- 14 October 2019, pp. 137-152
-
- Article
- Export citation
Enhanced function-means modeling supporting design space exploration
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
NLE volume 25 issue 6 Cover and Front matter
-
- Journal:
- Natural Language Engineering / Volume 25 / Issue 6 / November 2019
- Published online by Cambridge University Press:
- 11 October 2019, pp. f1-f2
-
- Article
-
- You have access
- Export citation
Editorial note
-
- Journal:
- Natural Language Engineering / Volume 25 / Issue 6 / November 2019
- Published online by Cambridge University Press:
- 11 October 2019, p. 675
-
- Article
-
- You have access
- HTML
- Export citation
NLE volume 25 issue 6 Cover and Back matter
-
- Journal:
- Natural Language Engineering / Volume 25 / Issue 6 / November 2019
- Published online by Cambridge University Press:
- 11 October 2019, pp. b1-b2
-
- Article
-
- You have access
- Export citation

Cracking the Digital Ceiling
-
- Published online:
- 10 October 2019
- Print publication:
- 24 October 2019
A Comparative Study of Some Central Notions of ASPIC+ and DeLP
-
- Journal:
- Theory and Practice of Logic Programming / Volume 20 / Issue 3 / May 2020
- Published online by Cambridge University Press:
- 10 October 2019, pp. 358-390
-
- Article
-
- You have access
- Open access
- Export citation
Mining, analyzing, and modeling text written on mobile devices
-
- Journal:
- Natural Language Engineering / Volume 27 / Issue 1 / January 2021
- Published online by Cambridge University Press:
- 10 October 2019, pp. 1-33
-
- Article
- Export citation
On sets of points with few odd secants
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 1 / January 2020
- Published online by Cambridge University Press:
- 10 October 2019, pp. 31-43
-
- Article
- Export citation
Compositional Specification in Rewriting Logic
-
- Journal:
- Theory and Practice of Logic Programming / Volume 20 / Issue 1 / January 2020
- Published online by Cambridge University Press:
- 09 October 2019, pp. 44-98
-
- Article
- Export citation
LOGIC AND TOPOLOGY FOR KNOWLEDGE, KNOWABILITY, AND BELIEF
-
- Journal:
- The Review of Symbolic Logic / Volume 13 / Issue 4 / December 2020
- Published online by Cambridge University Press:
- 09 October 2019, pp. 748-775
- Print publication:
- December 2020
-
- Article
- Export citation
A NOTE ON THE CUT-ELIMINATION PROOF IN “TRUTH WITHOUT CONTRA(DI)CTION”
-
- Journal:
- The Review of Symbolic Logic / Volume 13 / Issue 4 / December 2020
- Published online by Cambridge University Press:
- 09 October 2019, pp. 882-886
- Print publication:
- December 2020
-
- Article
- Export citation
Minimizing the number of 5-cycles in graphs with given edge-density
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 1 / January 2020
- Published online by Cambridge University Press:
- 09 October 2019, pp. 44-67
-
- Article
- Export citation
ROB volume 37 issue 11 Cover and Back matter
-
- Article
-
- You have access
- Export citation