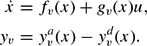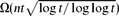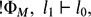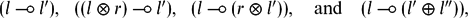Refine search
Actions for selected content:
48202 results in Computer Science
Analyzing heterogeneity in the effects of physical activity in children on social network structure and peer selection dynamics
-
- Journal:
- Network Science / Volume 4 / Issue 3 / September 2016
- Published online by Cambridge University Press:
- 12 May 2016, pp. 336-363
-
- Article
- Export citation
Corrigendum: Multi-contact bipedal robotic locomotion
-
- Article
-
- You have access
- Export citation
Friendship networks and sun safety behavior among children
-
- Journal:
- Network Science / Volume 4 / Issue 3 / September 2016
- Published online by Cambridge University Press:
- 10 May 2016, pp. 314-335
-
- Article
- Export citation
The co-evolution of power and friendship networks in an organization
-
- Journal:
- Network Science / Volume 4 / Issue 3 / September 2016
- Published online by Cambridge University Press:
- 10 May 2016, pp. 364-384
-
- Article
- Export citation
NERA 2.0: Improving coverage and performance of rule-based named entity recognition for Arabic*
-
- Journal:
- Natural Language Engineering / Volume 23 / Issue 3 / May 2017
- Published online by Cambridge University Press:
- 06 May 2016, pp. 441-472
-
- Article
- Export citation

Handbook of Computational Social Choice
-
- Published online:
- 05 May 2016
- Print publication:
- 25 April 2016
Asymptotic Structure of Graphs with the Minimum Number of Triangles
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 26 / Issue 1 / January 2017
- Published online by Cambridge University Press:
- 04 May 2016, pp. 138-160
-
- Article
-
- You have access
- Open access
- Export citation
Public investment and electric vehicle design: a model-based market analysis framework with application to a USA–China comparison study
- Part of
-
- Journal:
- Design Science / Volume 2 / 2016
- Published online by Cambridge University Press:
- 04 May 2016, e6
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
On the Richter–Thomassen Conjecture about Pairwise Intersecting Closed Curves†
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 25 / Issue 6 / November 2016
- Published online by Cambridge University Press:
- 04 May 2016, pp. 941-958
-
- Article
- Export citation
Shape Measures of Random Increasing k-trees†
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 25 / Issue 5 / September 2016
- Published online by Cambridge University Press:
- 04 May 2016, pp. 668-699
-
- Article
- Export citation
Range-based argumentation semantics as two-valued models
-
- Journal:
- Theory and Practice of Logic Programming / Volume 17 / Issue 1 / January 2017
- Published online by Cambridge University Press:
- 03 May 2016, pp. 75-90
-
- Article
- Export citation
The undecidability theorem for the Horn-like fragment of linear logic (Revisited)
-
- Journal:
- Mathematical Structures in Computer Science / Volume 26 / Issue 5 / June 2016
- Published online by Cambridge University Press:
- 03 May 2016, pp. 719-744
-
- Article
- Export citation
On definite program answers and least Herbrand models
-
- Journal:
- Theory and Practice of Logic Programming / Volume 16 / Issue 4 / July 2016
- Published online by Cambridge University Press:
- 03 May 2016, pp. 498-508
-
- Article
- Export citation
Enablers and inhibitors in causal justifications of logic programs*
-
- Journal:
- Theory and Practice of Logic Programming / Volume 17 / Issue 1 / January 2017
- Published online by Cambridge University Press:
- 03 May 2016, pp. 49-74
-
- Article
- Export citation
Realizability algebras III: some examples
-
- Journal:
- Mathematical Structures in Computer Science / Volume 28 / Issue 1 / January 2018
- Published online by Cambridge University Press:
- 03 May 2016, pp. 45-76
-
- Article
- Export citation