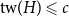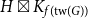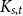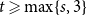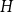Refine search
Actions for selected content:
52629 results in Statistics and Probability
Contents
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp vii-xiv
-
- Chapter
- Export citation
Appendix C - Statistical Tables
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp 666-687
-
- Chapter
- Export citation
Acknowledgments
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp xix-xx
-
- Chapter
- Export citation
Chapter Thirteen - One-Way Analysis of Variance
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp 401-438
-
- Chapter
- Export citation
Product structure of graph classes with bounded treewidth
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 33 / Issue 3 / May 2024
- Published online by Cambridge University Press:
- 07 December 2023, pp. 351-376
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Chapter Sixteen - An Introduction To Multiple Regression
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp 533-567
-
- Chapter
- Export citation
Chapter Eight - Theoretical Probability Models
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp 243-269
-
- Chapter
- Export citation
Chapter Eighteen - Nonparametric Methods
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp 595-626
-
- Chapter
- Export citation
Chapter Fourteen - Two-Way Analysis of Variance
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp 439-483
-
- Chapter
- Export citation
Chapter Five - Exploring Relationships between Two Variables
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp 148-194
-
- Chapter
- Export citation
Appendix B - .R Files and Datasets in R Format
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp 665-665
-
- Chapter
- Export citation
Appendix D - Solutions TO END-OF-CHAPTER EXERCISES
-
- Book:
- Statistics Using R
- Published online:
- 07 December 2023
- Print publication:
- 07 December 2023, pp 688-688
-
- Chapter
- Export citation
ACCI could be a poor prognostic indicator for the in-hospital mortality of patients with SFTS
-
- Journal:
- Epidemiology & Infection / Volume 151 / 2023
- Published online by Cambridge University Press:
- 06 December 2023, e203
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Weak convergence of the extremes of branching Lévy processes with regularly varying tails
- Part of
-
- Journal:
- Journal of Applied Probability / Volume 61 / Issue 2 / June 2024
- Published online by Cambridge University Press:
- 06 December 2023, pp. 622-643
- Print publication:
- June 2024
-
- Article
- Export citation
High prevalence of asymptomatic malaria in Forest Guinea: Results from a rapid community survey
-
- Journal:
- Epidemiology & Infection / Volume 152 / 2024
- Published online by Cambridge University Press:
- 05 December 2023, e1
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Analysis of a SARIMA-XGBoost model for hand, foot, and mouth disease in Xinjiang, China
-
- Journal:
- Epidemiology & Infection / Volume 151 / 2023
- Published online by Cambridge University Press:
- 04 December 2023, e200
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
APR volume 55 issue 4 Cover and Back matter
-
- Journal:
- Advances in Applied Probability / Volume 55 / Issue 4 / December 2023
- Published online by Cambridge University Press:
- 19 December 2023, pp. b1-b2
- Print publication:
- December 2023
-
- Article
-
- You have access
- Export citation
Speed of extinction for continuous-state branching processes in a weakly subcritical Lévy environment
- Part of
-
- Journal:
- Journal of Applied Probability / Volume 61 / Issue 3 / September 2024
- Published online by Cambridge University Press:
- 01 December 2023, pp. 886-908
- Print publication:
- September 2024
-
- Article
- Export citation
JPR volume 60 issue 4 Cover and Back matter
-
- Journal:
- Journal of Applied Probability / Volume 60 / Issue 4 / December 2023
- Published online by Cambridge University Press:
- 22 December 2023, pp. b1-b2
- Print publication:
- December 2023
-
- Article
-
- You have access
- Export citation
A subgeometric convergence formula for finite-level M/G/1-type Markov chains: via a block-decomposition-friendly solution to the Poisson equation of the deviation matrix
- Part of
-
- Journal:
- Advances in Applied Probability / Volume 56 / Issue 2 / June 2024
- Published online by Cambridge University Press:
- 01 December 2023, pp. 389-429
- Print publication:
- June 2024
-
- Article
- Export citation