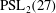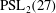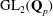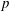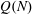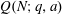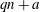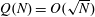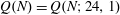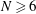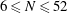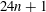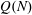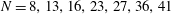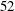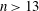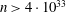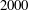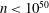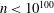Refine search
Actions for selected content:
48287 results in Computer Science
The influence of social networks and homophily on correct voting
-
- Journal:
- Network Science / Volume 2 / Issue 1 / April 2014
- Published online by Cambridge University Press:
- 03 April 2014, pp. 90-106
-
- Article
- Export citation
Sampling networks from their posterior predictive distribution
-
- Journal:
- Network Science / Volume 2 / Issue 1 / April 2014
- Published online by Cambridge University Press:
- 03 April 2014, pp. 107-131
-
- Article
- Export citation
A MACHINE-ASSISTED PROOF OF GÖDEL’S INCOMPLETENESS THEOREMS FOR THE THEORY OF HEREDITARILY FINITE SETS
-
- Journal:
- The Review of Symbolic Logic / Volume 7 / Issue 3 / September 2014
- Published online by Cambridge University Press:
- 03 April 2014, pp. 484-498
- Print publication:
- September 2014
-
- Article
- Export citation
Uncovering the structure and temporal dynamics of information propagation
-
- Journal:
- Network Science / Volume 2 / Issue 1 / April 2014
- Published online by Cambridge University Press:
- 03 April 2014, pp. 26-65
-
- Article
- Export citation
Classification of subgroups isomorphic to
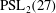 $\mathrm{PSL}_2(27)$ in the Monster
$\mathrm{PSL}_2(27)$ in the Monster
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 17 / Issue 1 / 2014
- Published online by Cambridge University Press:
- 01 April 2014, pp. 33-46
-
- Article
-
- You have access
- Export citation
MODALITY AND AXIOMATIC THEORIES OF TRUTH I: FRIEDMAN-SHEARD
-
- Journal:
- The Review of Symbolic Logic / Volume 7 / Issue 2 / June 2014
- Published online by Cambridge University Press:
- 01 April 2014, pp. 273-298
- Print publication:
- June 2014
-
- Article
- Export citation
Computing fundamental domains for the Bruhat–Tits tree for
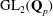 ${\rm GL}_2(\mathbf{Q}_p)$ ,
${\rm GL}_2(\mathbf{Q}_p)$ , 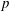 $p$ -adic automorphic forms, and the canonical embedding of Shimura curves
$p$ -adic automorphic forms, and the canonical embedding of Shimura curves
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 17 / Issue 1 / 2014
- Published online by Cambridge University Press:
- 01 April 2014, pp. 1-23
-
- Article
-
- You have access
- Export citation
MODALITY AND AXIOMATIC THEORIES OF TRUTH II: KRIPKE-FEFERMAN
-
- Journal:
- The Review of Symbolic Logic / Volume 7 / Issue 2 / June 2014
- Published online by Cambridge University Press:
- 01 April 2014, pp. 299-318
- Print publication:
- June 2014
-
- Article
- Export citation
On a conjecture of Rudin on squares in arithmetic progressions
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 17 / Issue 1 / 2014
- Published online by Cambridge University Press:
- 01 April 2014, pp. 58-76
-
- Article
-
- You have access
- Export citation
On the state complexity of semi-quantum finiteautomata⋆⋆⋆
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 48 / Issue 2 / April 2014
- Published online by Cambridge University Press:
- 17 April 2014, pp. 187-207
- Print publication:
- April 2014
-
- Article
- Export citation
Wieferich pairs and Barker sequences, II
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 17 / Issue 1 / 2014
- Published online by Cambridge University Press:
- 01 April 2014, pp. 24-32
-
- Article
-
- You have access
- Export citation
A scalable approach for ideation in biologically inspired design
-
- Article
-
- You have access
- HTML
- Export citation
Reuse of constraint knowledge bases and problem solvers explored in engineering design
-
- Article
-
- You have access
- HTML
- Export citation
A Generalized Model of PAC Learning and itsApplicability
-
- Journal:
- RAIRO - Theoretical Informatics and Applications / Volume 48 / Issue 2 / April 2014
- Published online by Cambridge University Press:
- 09 April 2014, pp. 209-245
- Print publication:
- April 2014
-
- Article
- Export citation