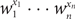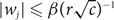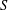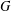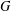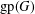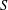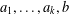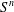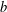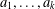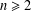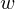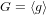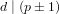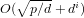Refine search
Actions for selected content:
30 results
The complexity of intersecting subproducts with subgroups in Cartesian powers
- Part of
-
- Journal:
- Glasgow Mathematical Journal , First View
- Published online by Cambridge University Press:
- 07 October 2025, pp. 1-7
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Vanishing of Schubert coefficients via the effective Hilbert nullstellensatz
- Part of
-
- Journal:
- Forum of Mathematics, Sigma / Volume 13 / 2025
- Published online by Cambridge University Press:
- 01 October 2025, e162
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Exact recovery of community detection in k-community Gaussian mixture models
- Part of
-
- Journal:
- European Journal of Applied Mathematics / Volume 36 / Issue 3 / June 2025
- Published online by Cambridge University Press:
- 18 September 2024, pp. 491-523
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Rigid continuation paths II. structured polynomial systems
- Part of
-
- Journal:
- Forum of Mathematics, Pi / Volume 11 / 2023
- Published online by Cambridge University Press:
- 14 April 2023, e12
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Functional norms, condition numbers and numerical algorithms in algebraic geometry
- Part of
-
- Journal:
- Forum of Mathematics, Sigma / Volume 10 / 2022
- Published online by Cambridge University Press:
- 22 November 2022, e103
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
IS CAUSAL REASONING HARDER THAN PROBABILISTIC REASONING?
- Part of
-
- Journal:
- The Review of Symbolic Logic / Volume 17 / Issue 1 / March 2024
- Published online by Cambridge University Press:
- 18 May 2022, pp. 106-131
- Print publication:
- March 2024
-
- Article
- Export citation
Yaglom limit for stochastic fluid models
- Part of
-
- Journal:
- Advances in Applied Probability / Volume 53 / Issue 3 / September 2021
- Published online by Cambridge University Press:
- 08 October 2021, pp. 649-686
- Print publication:
- September 2021
-
- Article
- Export citation
Polynomial-time approximation algorithms for the antiferromagnetic Ising model on line graphs
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 30 / Issue 6 / November 2021
- Published online by Cambridge University Press:
- 12 April 2021, pp. 905-921
-
- Article
- Export citation
DECIDING SOME MALTSEV CONDITIONS IN FINITE IDEMPOTENT ALGEBRAS
- Part of
-
- Journal:
- The Journal of Symbolic Logic / Volume 85 / Issue 2 / June 2020
- Published online by Cambridge University Press:
- 16 June 2020, pp. 539-562
- Print publication:
- June 2020
-
- Article
- Export citation
Estimating parameters associated with monotone properties
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 4 / July 2020
- Published online by Cambridge University Press:
- 24 March 2020, pp. 616-632
-
- Article
- Export citation
Deciding the Existence of Minority Terms
- Part of
-
- Journal:
- Canadian Mathematical Bulletin / Volume 63 / Issue 3 / September 2020
- Published online by Cambridge University Press:
- 24 October 2019, pp. 577-591
- Print publication:
- September 2020
-
- Article
-
- You have access
- Export citation
DEGREE BOUNDED GEOMETRIC SPANNING TREES WITH A BOTTLENECK OBJECTIVE FUNCTION
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 101 / Issue 1 / February 2020
- Published online by Cambridge University Press:
- 23 October 2019, pp. 170-171
- Print publication:
- February 2020
-
- Article
-
- You have access
- Export citation
Weighted counting of solutions to sparse systems of equations
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 28 / Issue 5 / September 2019
- Published online by Cambridge University Press:
- 15 April 2019, pp. 696-719
-
- Article
- Export citation
ON FINDING SOLUTIONS TO EXPONENTIAL CONGRUENCES
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 99 / Issue 3 / June 2019
- Published online by Cambridge University Press:
- 27 December 2018, pp. 388-391
- Print publication:
- June 2019
-
- Article
-
- You have access
- Export citation
Dual-Pivot Quicksort: Optimality, Analysis and Zeros of Associated Lattice Paths
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 28 / Issue 4 / July 2019
- Published online by Cambridge University Press:
- 14 August 2018, pp. 485-518
-
- Article
- Export citation
A GENERAL POSITION PROBLEM IN GRAPH THEORY
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 98 / Issue 2 / October 2018
- Published online by Cambridge University Press:
- 18 July 2018, pp. 177-187
- Print publication:
- October 2018
-
- Article
-
- You have access
- Export citation
ON SEMIGROUPS WITH PSPACE-COMPLETE SUBPOWER MEMBERSHIP PROBLEM
- Part of
-
- Journal:
- Journal of the Australian Mathematical Society / Volume 106 / Issue 1 / February 2019
- Published online by Cambridge University Press:
- 30 May 2018, pp. 127-142
- Print publication:
- February 2019
-
- Article
-
- You have access
- Export citation
Reduced memory meet-in-the-middle attackagainst the NTRU private key
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 19 / Issue A / 2016
- Published online by Cambridge University Press:
- 26 August 2016, pp. 43-57
-
- Article
-
- You have access
- Export citation
An algorithm for NTRU problems and cryptanalysis of the GGH multilinear map without a low-level encoding of zero
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 19 / Issue A / 2016
- Published online by Cambridge University Press:
- 26 August 2016, pp. 255-266
-
- Article
-
- You have access
- Export citation
A new approach to the discrete logarithm problem with auxiliary inputs
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 19 / Issue 1 / 2016
- Published online by Cambridge University Press:
- 01 January 2016, pp. 1-15
-
- Article
-
- You have access
- Export citation