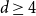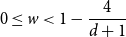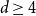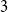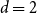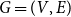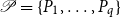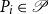Refine search
Actions for selected content:
48290 results in Computer Science
Leveraging machine translation for cross-lingual fine-grained cyberbullying classification amongst pre-adolescents
-
- Journal:
- Natural Language Engineering / Volume 29 / Issue 6 / November 2023
- Published online by Cambridge University Press:
- 07 September 2022, pp. 1458-1480
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Effects of electrostriction on the bifurcated electro-mechanical performance of conical dielectric elastomer actuators and sensors
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
On improved fail-safe sensor distributions for a structural health monitoring system
- Part of
-
- Journal:
- Data-Centric Engineering / Volume 3 / 2022
- Published online by Cambridge University Press:
- 07 September 2022, e27
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Uniqueness of the Gibbs measure for the 4-state anti-ferromagnetic Potts model on the regular tree
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 32 / Issue 1 / January 2023
- Published online by Cambridge University Press:
- 07 September 2022, pp. 158-182
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Detection and diagnosis of deviations in distributed systems of autonomous agents
-
- Journal:
- Mathematical Structures in Computer Science / Volume 32 / Issue 9 / October 2022
- Published online by Cambridge University Press:
- 06 September 2022, pp. 1254-1282
-
- Article
- Export citation
Connectivity-preserving distributed algorithms for removing links in directed networks
-
- Journal:
- Network Science / Volume 10 / Issue 3 / September 2022
- Published online by Cambridge University Press:
- 06 September 2022, pp. 215-233
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
A journey toward an open data culture through transformation of shared data into a data resource
-
- Journal:
- Data & Policy / Volume 4 / 2022
- Published online by Cambridge University Press:
- 06 September 2022, e29
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Application of offset estimator of differential entropy and mutual information with multivariate data
-
- Journal:
- Experimental Results / Volume 3 / 2022
- Published online by Cambridge University Press:
- 05 September 2022, e16
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Supporting peace negotiations in the Yemen war through machine learning
-
- Journal:
- Data & Policy / Volume 4 / 2022
- Published online by Cambridge University Press:
- 02 September 2022, e28
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Radical Creative Semantic Anchoring: Creative-action metaphors and timbral interaction
-
- Journal:
- Organised Sound / Volume 28 / Issue 1 / April 2023
- Published online by Cambridge University Press:
- 02 September 2022, pp. 64-77
- Print publication:
- April 2023
-
- Article
- Export citation
A new comprehensive performance optimization approach for Earth-contact mechanism based on terrain-adaptability task
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Reconfigurable fully constrained cable-driven parallel mechanism for avoiding collision between cables with human
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
On Petrie cycle and Petrie tour partitions of 3- and 4-regular plane graphs
-
- Journal:
- Mathematical Structures in Computer Science / Volume 32 / Issue 2 / February 2022
- Published online by Cambridge University Press:
- 30 August 2022, pp. 240-256
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
Techniques for blocking the propagation of two simultaneous contagions over networks using a graph dynamical systems framework
-
- Journal:
- Network Science / Volume 10 / Issue 3 / September 2022
- Published online by Cambridge University Press:
- 30 August 2022, pp. 234-260
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
A sensitivity analysis of a regression model of ocean temperature
-
- Journal:
- Environmental Data Science / Volume 1 / 2022
- Published online by Cambridge University Press:
- 30 August 2022, e11
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
From theories on styles to their transfer in text: Bridging the gap with a hierarchical survey
-
- Journal:
- Natural Language Engineering / Volume 29 / Issue 4 / July 2023
- Published online by Cambridge University Press:
- 26 August 2022, pp. 849-908
-
- Article
-
- You have access
- Open access
- HTML
- Export citation
RoLEX: The development of an extended Romanian lexical dataset and its evaluation at predicting concurrent lexical information
-
- Journal:
- Natural Language Engineering / Volume 29 / Issue 3 / May 2023
- Published online by Cambridge University Press:
- 26 August 2022, pp. 720-745
-
- Article
- Export citation