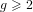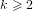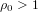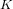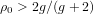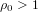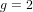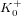Refine listing
Actions for selected content:
112 results in 11Txx
RIGID LOCAL SYSTEMS ON
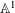 $\mathbb{A}^{1}$ WITH FINITE MONODROMY
$\mathbb{A}^{1}$ WITH FINITE MONODROMY
- Part of
-
- Journal:
- Mathematika / Volume 64 / Issue 3 / 2018
- Published online by Cambridge University Press:
- 01 August 2018, pp. 785-846
- Print publication:
- 2018
-
- Article
- Export citation
TERNARY DIVISOR FUNCTIONS IN ARITHMETIC PROGRESSIONS TO SMOOTH MODULI
- Part of
-
- Journal:
- Mathematika / Volume 64 / Issue 3 / 2018
- Published online by Cambridge University Press:
- 19 June 2018, pp. 701-729
- Print publication:
- 2018
-
- Article
- Export citation
MULTIPLICATIVE ORDERS IN ORBITS OF POLYNOMIALS OVER FINITE FIELDS
- Part of
-
- Journal:
- Glasgow Mathematical Journal / Volume 60 / Issue 2 / May 2018
- Published online by Cambridge University Press:
- 23 October 2017, pp. 487-493
- Print publication:
- May 2018
-
- Article
-
- You have access
- Export citation
Fast Evaluation of the Caputo Fractional Derivative and its Applications to Fractional Diffusion Equations: A Second-Order Scheme
- Part of
- Computational aspects
- Partial differential equations, initial value and time-dependent initial-boundary value problems
- General theory in ordinary differential equations
- Real functions
- Finite fields and commutative rings (number-theoretic aspects)
- Miscellaneous topics - Partial differential equations
-
- Journal:
- Communications in Computational Physics / Volume 22 / Issue 4 / October 2017
- Published online by Cambridge University Press:
- 28 July 2017, pp. 1028-1048
- Print publication:
- October 2017
-
- Article
- Export citation
ITERATION OF QUADRATIC POLYNOMIALS OVER FINITE FIELDS
- Part of
-
- Journal:
- Mathematika / Volume 63 / Issue 3 / 2017
- Published online by Cambridge University Press:
- 29 November 2017, pp. 1041-1059
- Print publication:
- 2017
-
- Article
- Export citation
ON SOME MULTIPLE CHARACTER SUMS
- Part of
-
- Journal:
- Mathematika / Volume 63 / Issue 2 / 2017
- Published online by Cambridge University Press:
- 03 April 2017, pp. 553-560
- Print publication:
- 2017
-
- Article
- Export citation
THE HOLOMORPHY CONJECTURE FOR NONDEGENERATE SURFACE SINGULARITIES
- Part of
-
- Journal:
- Nagoya Mathematical Journal / Volume 227 / September 2017
- Published online by Cambridge University Press:
- 28 October 2016, pp. 160-188
- Print publication:
- September 2017
-
- Article
-
- You have access
- HTML
- Export citation
On the Bateman–Horn conjecture for polynomials over large finite fields
- Part of
-
- Journal:
- Compositio Mathematica / Volume 152 / Issue 12 / December 2016
- Published online by Cambridge University Press:
- 21 September 2016, pp. 2525-2544
- Print publication:
- December 2016
-
- Article
- Export citation
On error distributions in ring-based LWE
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 19 / Issue A / 2016
- Published online by Cambridge University Press:
- 26 August 2016, pp. 130-145
-
- Article
-
- You have access
- Export citation
Collecting relations for the number field sieve in
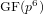 $\text{GF}(p^{6})$
$\text{GF}(p^{6})$
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 19 / Issue A / 2016
- Published online by Cambridge University Press:
- 26 August 2016, pp. 332-350
-
- Article
-
- You have access
- Export citation
Reduced memory meet-in-the-middle attackagainst the NTRU private key
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 19 / Issue A / 2016
- Published online by Cambridge University Press:
- 26 August 2016, pp. 43-57
-
- Article
-
- You have access
- Export citation
Roots of sparse polynomials over a finite field
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 19 / Issue A / 2016
- Published online by Cambridge University Press:
- 26 August 2016, pp. 196-204
-
- Article
-
- You have access
- Export citation
Kloosterman paths and the shape of exponential sums
- Part of
-
- Journal:
- Compositio Mathematica / Volume 152 / Issue 7 / July 2016
- Published online by Cambridge University Press:
- 15 April 2016, pp. 1489-1516
- Print publication:
- July 2016
-
- Article
- Export citation
COUNTING POINTS ON DWORK HYPERSURFACES AND
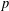 $p$ -ADIC HYPERGEOMETRIC FUNCTIONS
$p$ -ADIC HYPERGEOMETRIC FUNCTIONS
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 94 / Issue 2 / October 2016
- Published online by Cambridge University Press:
- 17 February 2016, pp. 208-216
- Print publication:
- October 2016
-
- Article
-
- You have access
- Export citation
THE DIVISOR FUNCTION IN ARITHMETIC PROGRESSIONS MODULO PRIME POWERS
- Part of
-
- Journal:
- Mathematika / Volume 62 / Issue 3 / 2016
- Published online by Cambridge University Press:
- 17 May 2016, pp. 898-908
- Print publication:
- 2016
-
- Article
- Export citation
PRIMITIVE PRIME DIVISORS AND THE
 $\mathbf{n}$ TH CYCLOTOMIC POLYNOMIAL
$\mathbf{n}$ TH CYCLOTOMIC POLYNOMIAL
- Part of
-
- Journal:
- Journal of the Australian Mathematical Society / Volume 102 / Issue 1 / February 2017
- Published online by Cambridge University Press:
- 04 November 2015, pp. 122-135
- Print publication:
- February 2017
-
- Article
-
- You have access
- Export citation
MORE CONSTRUCTIONS OF APPROXIMATELY MUTUALLY UNBIASED BASES
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 93 / Issue 2 / April 2016
- Published online by Cambridge University Press:
- 17 August 2015, pp. 211-222
- Print publication:
- April 2016
-
- Article
-
- You have access
- Export citation
Groups generated by iterations of polynomials over finite fields
- Part of
-
- Journal:
- Proceedings of the Edinburgh Mathematical Society / Volume 59 / Issue 1 / February 2016
- Published online by Cambridge University Press:
- 05 June 2015, pp. 235-245
-
- Article
- Export citation
Heuristics on pairing-friendly abelian varieties
- Part of
-
- Journal:
- LMS Journal of Computation and Mathematics / Volume 18 / Issue 1 / 2015
- Published online by Cambridge University Press:
- 01 June 2015, pp. 419-443
-
- Article
-
- You have access
- Export citation
A NOTE ON SOME CHARACTER SUMS OVER FINITE FIELDS
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 92 / Issue 1 / August 2015
- Published online by Cambridge University Press:
- 30 April 2015, pp. 32-43
- Print publication:
- August 2015
-
- Article
-
- You have access
- Export citation
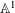
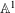
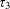
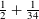
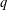
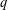
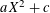
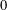
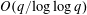
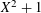
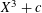
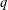
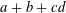
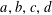
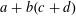
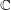
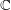
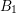

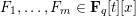
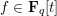
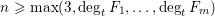


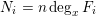
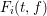
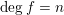
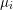
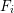
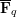
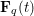
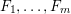


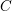
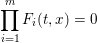
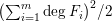
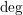
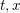
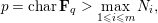
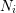
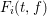
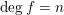
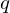
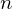
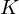
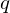
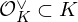
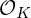
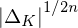
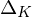
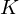
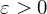
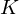
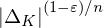
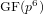
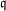
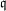
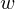
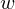
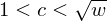
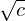
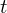
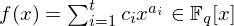
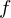
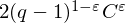
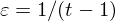
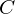
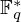
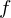
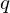
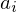
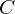
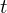
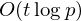
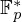
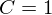
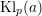

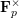
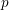
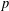
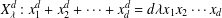
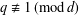
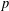
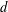
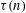
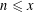
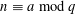
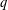
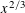
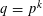
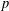
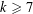


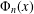
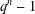
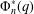

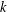

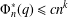
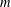
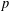
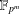
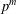
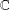
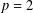
 of q elements, we consider a trajectory of the map
of q elements, we consider a trajectory of the map 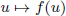 associated with a polynomial
associated with a polynomial  ]. Using bounds of character sums, under some mild condition on
]. Using bounds of character sums, under some mild condition on 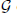 of
of 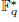 , improving the trivial lower bound
, improving the trivial lower bound 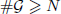 . Using a different technique, we also obtain a similar result for very small values of
. Using a different technique, we also obtain a similar result for very small values of