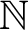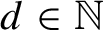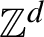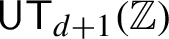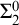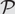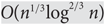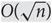Refine listing
Actions for selected content:
124 results in 68Qxx
Computable Følner monotilings and a theorem of Brudno
- Part of
-
- Journal:
- Ergodic Theory and Dynamical Systems / Volume 41 / Issue 11 / November 2021
- Published online by Cambridge University Press:
- 13 November 2020, pp. 3389-3416
- Print publication:
- November 2021
-
- Article
- Export citation
Tail bounds on hitting times of randomized search heuristics using variable drift analysis
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 30 / Issue 4 / July 2021
- Published online by Cambridge University Press:
- 05 November 2020, pp. 550-569
-
- Article
-
- You have access
- Export citation
INFINITE STRINGS AND THEIR LARGE SCALE PROPERTIES
- Part of
-
- Journal:
- The Journal of Symbolic Logic / Volume 87 / Issue 2 / June 2022
- Published online by Cambridge University Press:
- 30 October 2020, pp. 585-625
- Print publication:
- June 2022
-
- Article
- Export citation
MODEL THEORY AND COMBINATORICS OF BANNED SEQUENCES
- Part of
-
- Journal:
- The Journal of Symbolic Logic / Volume 87 / Issue 1 / March 2022
- Published online by Cambridge University Press:
- 05 October 2020, pp. 1-20
- Print publication:
- March 2022
-
- Article
- Export citation
Inessential directed maps and directed homotopy equivalences
- Part of
-
- Journal:
- Proceedings of the Royal Society of Edinburgh. Section A: Mathematics / Volume 151 / Issue 4 / August 2021
- Published online by Cambridge University Press:
- 25 September 2020, pp. 1383-1406
- Print publication:
- August 2021
-
- Article
- Export citation
A SCHEMATIC DEFINITION OF QUANTUM POLYNOMIAL TIME COMPUTABILITY
- Part of
-
- Journal:
- The Journal of Symbolic Logic / Volume 85 / Issue 4 / December 2020
- Published online by Cambridge University Press:
- 08 September 2020, pp. 1546-1587
- Print publication:
- December 2020
-
- Article
- Export citation
THE LOGIC OF INFORMATION IN STATE SPACES
- Part of
-
- Journal:
- The Review of Symbolic Logic / Volume 14 / Issue 1 / March 2021
- Published online by Cambridge University Press:
- 25 August 2020, pp. 155-186
- Print publication:
- March 2021
-
- Article
- Export citation
CATEGORICAL COMPLEXITY
- Part of
-
- Journal:
- Forum of Mathematics, Sigma / Volume 8 / 2020
- Published online by Cambridge University Press:
- 30 June 2020, e34
-
- Article
-
- You have access
- Open access
- Export citation
COMPOSITIONALITY, COMPUTABILITY, AND COMPLEXITY
- Part of
-
- Journal:
- The Review of Symbolic Logic / Volume 14 / Issue 3 / September 2021
- Published online by Cambridge University Press:
- 29 June 2020, pp. 551-591
- Print publication:
- September 2021
-
- Article
- Export citation
GÖDEL’S SECOND INCOMPLETENESS THEOREM: HOW IT IS DERIVED AND WHAT IT DELIVERS
- Part of
-
- Journal:
- Bulletin of Symbolic Logic / Volume 26 / Issue 3-4 / December 2020
- Published online by Cambridge University Press:
- 10 June 2020, pp. 241-256
- Print publication:
- December 2020
-
- Article
- Export citation
DECIDING SOME MALTSEV CONDITIONS IN FINITE IDEMPOTENT ALGEBRAS
- Part of
-
- Journal:
- The Journal of Symbolic Logic / Volume 85 / Issue 2 / June 2020
- Published online by Cambridge University Press:
- 16 June 2020, pp. 539-562
- Print publication:
- June 2020
-
- Article
- Export citation
Eventually dendric shift spaces
- Part of
-
- Journal:
- Ergodic Theory and Dynamical Systems / Volume 41 / Issue 7 / July 2021
- Published online by Cambridge University Press:
- 26 May 2020, pp. 2023-2048
- Print publication:
- July 2021
-
- Article
- Export citation
Pointer chasing via triangular discrimination
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 4 / July 2020
- Published online by Cambridge University Press:
- 15 May 2020, pp. 485-494
-
- Article
-
- You have access
- Open access
- Export citation
Estimating parameters associated with monotone properties
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 4 / July 2020
- Published online by Cambridge University Press:
- 24 March 2020, pp. 616-632
-
- Article
- Export citation
The replica symmetric phase of random constraint satisfaction problems
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 3 / May 2020
- Published online by Cambridge University Press:
- 03 December 2019, pp. 346-422
-
- Article
- Export citation
A LEARNING-THEORETIC CHARACTERISATION OF MARTIN-LÖF RANDOMNESS AND SCHNORR RANDOMNESS
- Part of
-
- Journal:
- The Review of Symbolic Logic / Volume 14 / Issue 2 / June 2021
- Published online by Cambridge University Press:
- 04 November 2019, pp. 531-549
- Print publication:
- June 2021
-
- Article
- Export citation
The string of diamonds is nearly tight for rumour spreading
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 29 / Issue 2 / March 2020
- Published online by Cambridge University Press:
- 04 November 2019, pp. 190-199
-
- Article
- Export citation
Deciding the Existence of Minority Terms
- Part of
-
- Journal:
- Canadian Mathematical Bulletin / Volume 63 / Issue 3 / September 2020
- Published online by Cambridge University Press:
- 24 October 2019, pp. 577-591
- Print publication:
- September 2020
-
- Article
-
- You have access
- Export citation
DEGREE BOUNDED GEOMETRIC SPANNING TREES WITH A BOTTLENECK OBJECTIVE FUNCTION
- Part of
-
- Journal:
- Bulletin of the Australian Mathematical Society / Volume 101 / Issue 1 / February 2020
- Published online by Cambridge University Press:
- 23 October 2019, pp. 170-171
- Print publication:
- February 2020
-
- Article
-
- You have access
- Export citation
A natural barrier in random greedy hypergraph matching
- Part of
-
- Journal:
- Combinatorics, Probability and Computing / Volume 28 / Issue 6 / November 2019
- Published online by Cambridge University Press:
- 27 June 2019, pp. 816-825
-
- Article
- Export citation